New Phishing Scam Exploits Google Drawings and WhatsApp Links to Steal Sensitive Info

Cybersecurity researchers have uncovered a sophisticated phishing campaign that utilizes Google Drawings and WhatsApp shortened links to evade detection and trick users into divulging sensitive information. This novel attack highlights the evolving tactics employed by threat actors to bypass security measures and exploit trust in legitimate services.
The Attack
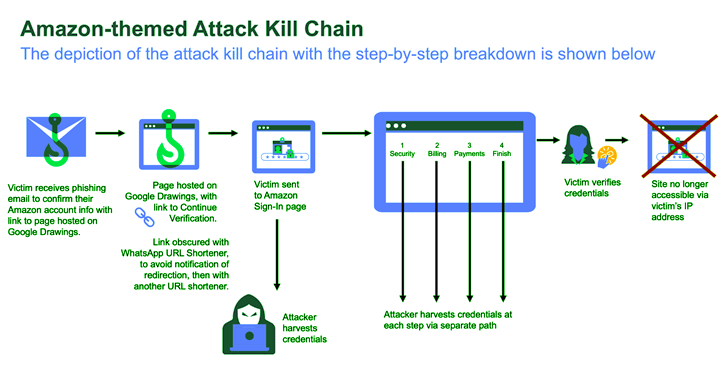
The phishing campaign begins with an email directing recipients to a graphic hosted on Google Drawings, masquerading as an Amazon account verification link. This initial step leverages Google's trusted reputation to evade detection. This contains a link that, when clicked, redirects users to a fake Amazon login page. This page is designed to harvest credentials, personal information, and credit card details.
Evasion Techniques
To further obfuscate the attack, the URL is shortened using two different URL shorteners: WhatsApp ("l.wl[.]co") followed by qrco[.]de. This multi-layered approach deceives security URL scanners and makes it challenging for users to identify the phishing attempt.
Exploiting Trust
The use of Google Drawings and WhatsApp links exploits the trust users have in these legitimate services. By hosting the attack elements on trusted platforms, attackers can bypass security measures and increase the likelihood of users clicking on the bogus links.
Microsoft 365 Anti-Phishing Loophole
In a related development, researchers have identified a loophole in Microsoft 365's anti-phishing mechanisms. This vulnerability allows attackers to hide the "First Contact Safety Tip" using CSS trickery, increasing the risk of users opening phishing emails. Microsoft has acknowledged the issue but has yet to release a fix.
Stay Vigilant
This phishing campaign serves as a reminder to remain cautious when interacting with links and emails, even if they appear to come from trusted sources. Users must be vigilant and verify the authenticity of requests for sensitive information. Organizations should also reinforce security measures and educate employees on the latest phishing tactics.
Protect Yourself
- Be cautious with links and emails from unknown sources
- Verify the authenticity of requests for sensitive information
- Use two-factor authentication whenever possible
- Install Net Protector Antivirus and protect your privacy






