Over 90 Malicious Android Apps with 5.5M Installs Found on Google Play

In a recent alarming discovery, over 90 malicious Android apps have been identified on Google Play, amassing more than 5.5 million installations. These apps are delivering malware and adware, with the Anatsa banking trojan seeing a significant resurgence.
Anatsa Trojan: A Renewed Threat
Anatsa, also known as "Teabot," is a banking trojan targeting over 650 financial applications across Europe, the US, the UK, and Asia. This malware aims to steal e-banking credentials to perform fraudulent transactions. According to Threat Fabric, since late last year, Anatsa has infected at least 150,000 devices via decoy productivity apps on Google Play.
Recent Findings by Zscaler
In February 2024, Zscaler reported that Anatsa had reappeared on Google Play, distributed through two decoy applications: 'PDF Reader & File Manager' and 'QR Reader & File Manager.' These apps had already amassed 70,000 installations by the time of analysis, highlighting the persistent risk of malicious dropper apps bypassing Google's review process.
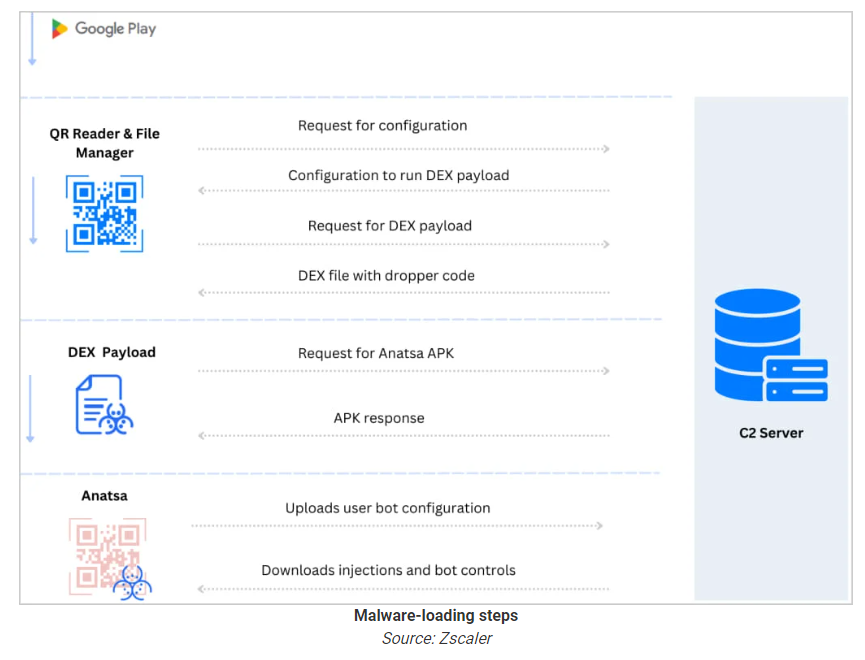
Multi-Stage Payload Loading Mechanism
One of the techniques Anatsa uses to evade detection is a multi-stage payload loading mechanism involving four distinct steps:
Configuration Retrieval: The dropper app retrieves configuration and essential strings from the Command-and-Control (C2) server.
Malicious Code Activation: A DEX file containing malicious dropper code is downloaded and activated on the device.
Payload URL Download: A configuration file with the Anatsa payload URL is downloaded.
Malware Installation: The DEX file fetches and installs the malware payload (APK), completing the infection.
Additionally, the DEX file performs anti-analysis checks to ensure the malware isn't executed in sandboxes or emulated environments. Once active, Anatsa uploads bot configuration and app scan results, then downloads injections that match the victim's location and profile.
Other Google Play Threats
Over the past few months, Zscaler discovered more than 90 malicious applications on Google Play, which collectively gathered 5.5 million installations. These apps masqueraded as tools, personalization apps, photography utilities, productivity, and health & fitness apps. The dominant malware families include Joker, Facestealer, Anatsa, Coper, and various others.
Despite Anatsa and Coper accounting for only 3% of the total malicious downloads, they are notably more dangerous, capable of performing on-device fraud and stealing sensitive information.
Protecting Yourself
To protect against such threats, users should:
Review Permissions: Carefully review the permissions requested by new apps and decline those associated with high-risk activities, such as Accessibility Service, SMS, and contacts list.
Use Google Play Protect: Ensure Google Play Protect is enabled to automatically remove or disable known malicious apps.
Google’s Response
At the time of writing, the two Anatsa dropper apps identified by Zscaler have been removed from Google Play. A Google spokesperson confirmed to BleepingComputer that the developers behind these malicious apps have been banned. They issued the following statement:
"All of the identified malicious apps have been removed from Google Play. Google Play Protect also protects users by automatically removing or disabling apps known to contain this malware on Android devices with Google Play Services."
The discovery of over 90 malicious apps on Google Play underscores the ongoing challenge of keeping the platform secure. Users must stay vigilant, regularly review app permissions, and rely on security features like Google Play Protect to defend against such threats.
Stay informed and cautious when downloading new apps to ensure your device and personal information remain secure.






