fp-3a
-
Read moreExplore how the Underground ransomware gang is enhancing tactics against global organizations, using advanced encryption and targeted attacks.
-
Read moreZimperium’s zLabs has uncovered a new variant of the Hook Android banking trojan, featuring ransomware-style overlays and advanced credential theft tactics. Learn about its key features and technical insights.
-
Read moreAdversaries are misusing AI-powered website builders like Lovable to create malicious infrastructure for malware distribution and credential phishing. Discover the emerging threats and how organizations can protect themselves.
-
Read moreExplore the resurgence of trojan horses powered by Large Language Models (LLMs). Learn how these threats disguise themselves as legitimate applications, embedding malicious capabilities that challenge traditional defenses.
-
Read moreDiscover how the new GodRAT malware, derived from the Gh0st RAT codebase, infiltrates financial institutions using malicious screensaver and program files. Learn about its evolution and impact on security.
-
Read moreAllianz Life confirms a major data breach affecting 1.1 million customers. Learn about the stolen information, the hacking group behind the attack, and the risks of identity theft.
-
Read moreMicrosoft warns of a counterfeit ChatGPT Desktop app delivering PipeMagic malware, a modular backdoor linked to ransomware. Learn how to protect yourself from this cyber threat.
-
Read moreDiscover how a Pakistan-based cybercrime network exploited pirated software to infect 1.88 million devices and steal $4.67 million in credentials. Learn about their tactics and operation details.
-
Read moreDiscover how artificial intelligence is reshaping phishing tactics in cybercrime. Learn about AI-driven scams, deepfake technology, and the exploitation of messaging platforms.
-
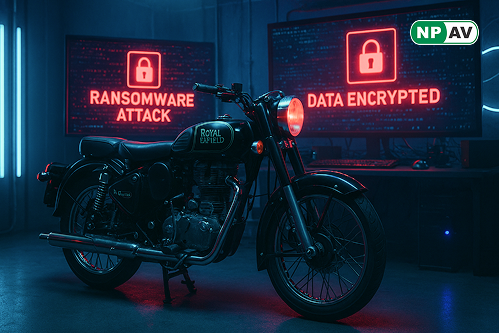
Read moreRoyal Enfield faces a significant ransomware attack, with hackers claiming full system compromise and demanding ransom. Learn about the implications and response.