Monthly Archives: September 2020
-
Read more
Researchers have discovered an all new credit card skimming campaign stealing funds.
Read moreHackers have started a new campaign to infect user systems via phishing emails.
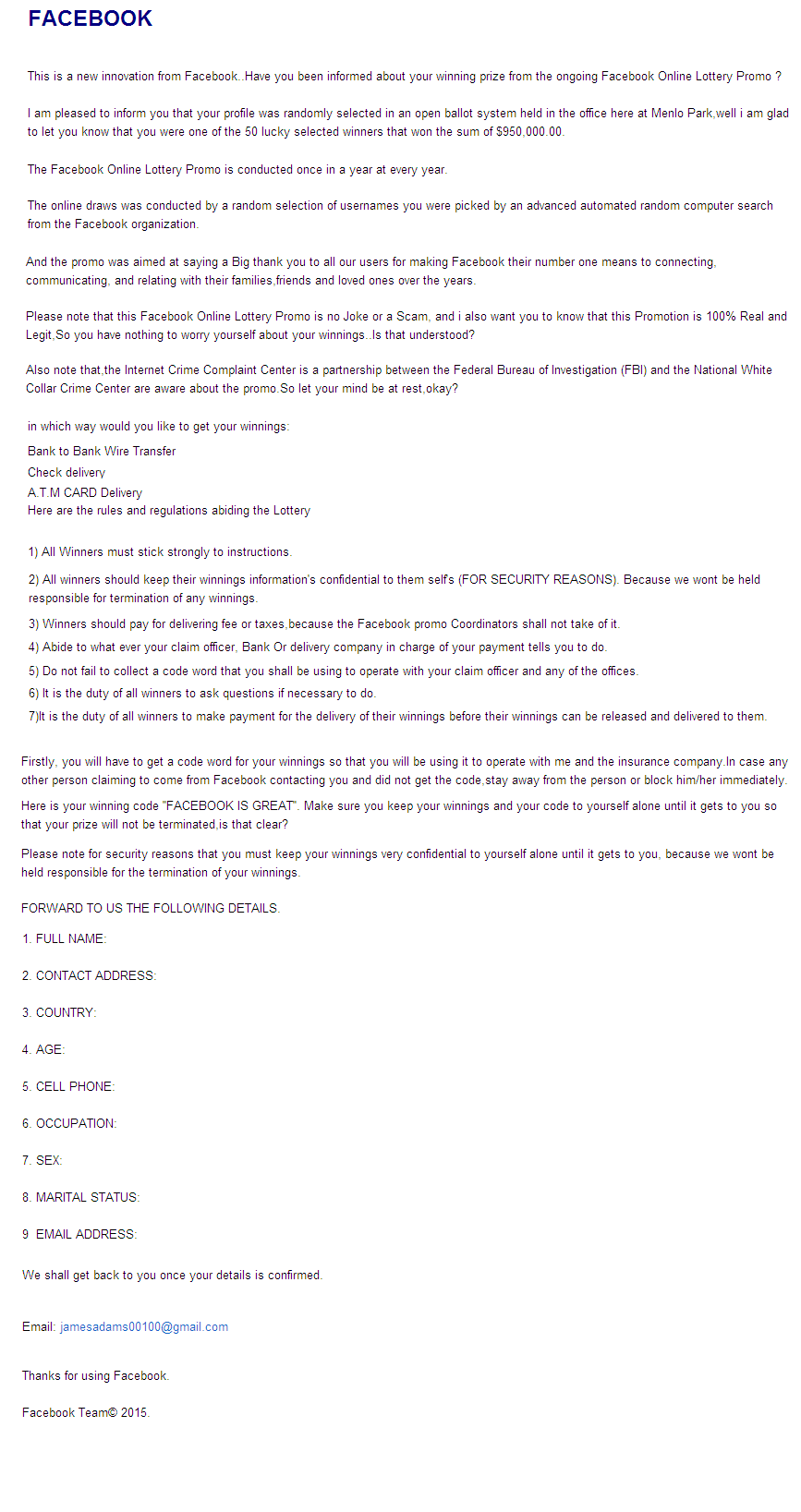
Read morePhishing scams continue to target users and steal their credentials by sending fake email alerts.
Read moreHackers have started exploiting this vulnerability to steal from user credit cards for their benefit.
Back to Top