Beware! Fake AI-Generated GitHub Repositories Stealing Sensitive Data

A new cyber threat is targeting developers and online users through AI-generated fake GitHub repositories. Attackers are using deceptive documentation and hidden malware to steal sensitive data, including login credentials, cryptocurrency wallets, and two-factor authentication (2FA) codes.
- Fake GitHub Repositories: Cybercriminals create AI-generated repositories that look real, using professional documentation, emojis, and logos to gain user trust.
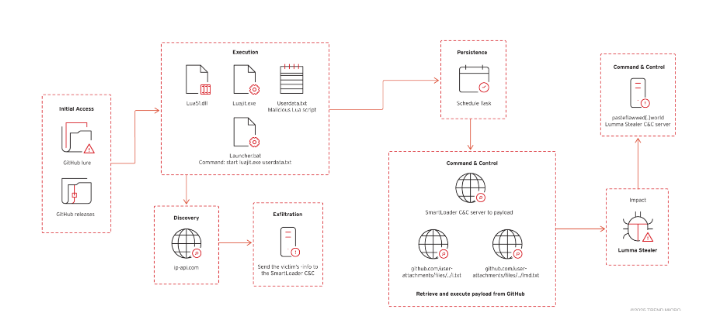
- Hidden Malware in Downloads: Malicious ZIP files in the Releases section contain SmartLoader, which delivers Lumma Stealer, a powerful data-stealing malware.
- Targeted Victims: Users searching for gaming mods, cracked software, or cryptocurrency tools are tricked into downloading the infected files.
- Data Theft: The malware steals browser credentials, session cookies, crypto wallets, clipboard content, and system data for further attacks.
- Evasive Techniques: Attackers use obfuscation, sandbox detection, and multi-stage payloads to bypass security measures.
This attack highlights the growing sophistication of AI-driven cyber threats. Hackers are now leveraging legitimate platforms like GitHub to spread malware, making it harder to detect. Organizations and individual users must remain vigilant, follow strict cybersecurity practices, and use trusted security solutions like Net Protector to stay protected from evolving threats.
Comment(s)






