Dangerous Email Scam Steals Office365 Credentials and Installs Malware – Be Alert!
A new email-based cyberattack tricks users into either giving away their Office365 login details or installing malware disguised as a Microsoft app. The attack uses trusted platforms like files.fm to appear legitimate and targets businesses and professionals using a double-threat strategy.
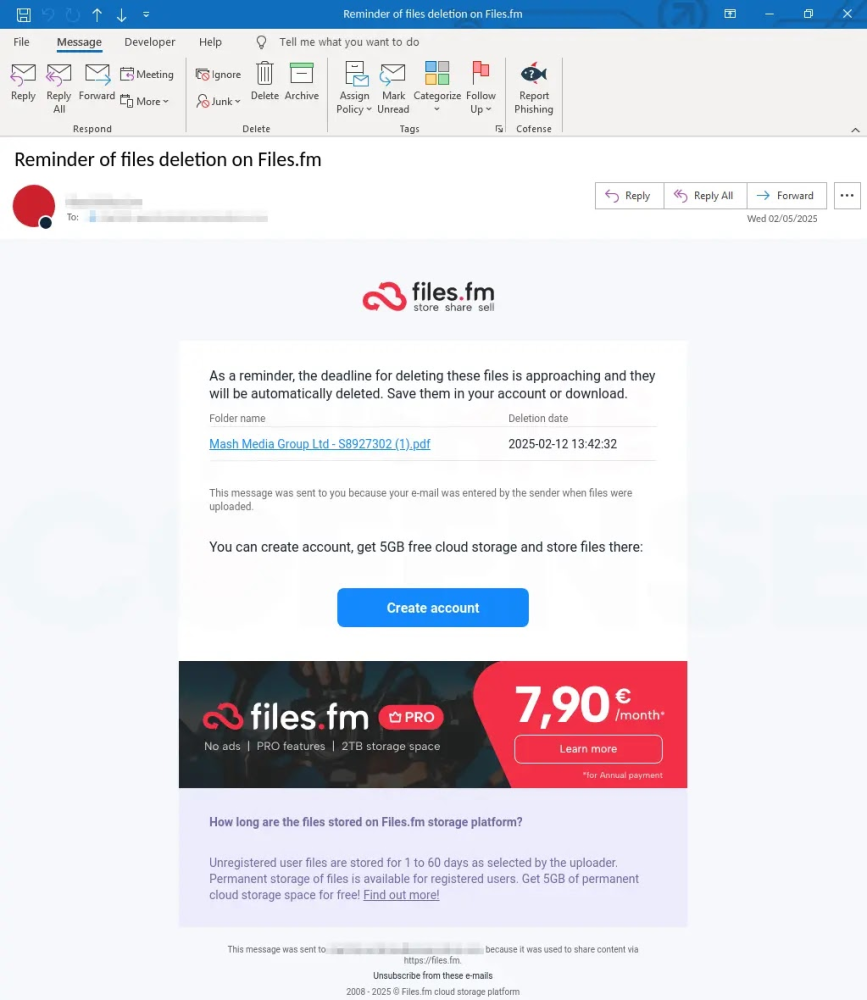
- Two-Pronged Attack: Victims receive emails pretending to warn about deleted documents. The links lead to files on files.fm, a trusted file-sharing site.
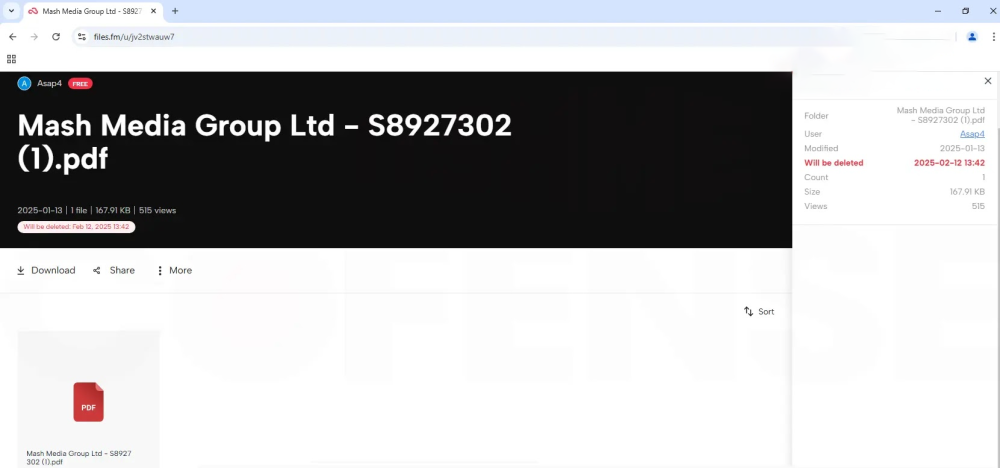
- Credential Theft via "Preview": Clicking "Preview" in the PDF redirects to a fake Microsoft login page. If users enter their login details, attackers steal them instantly.
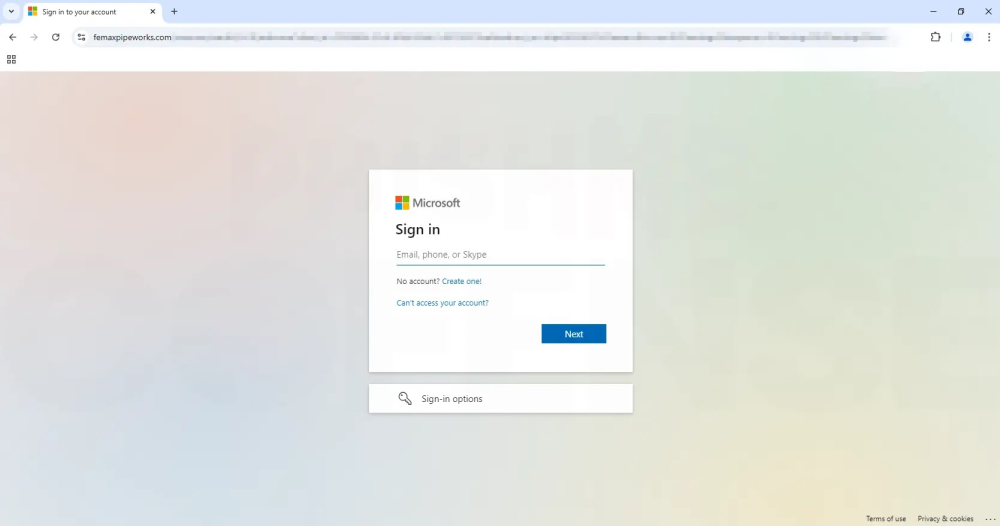
- Malware via "Download": Clicking "Download" triggers installation of a fake Microsoft app named SecuredOneDrive.ClientSetup.exe, which actually deploys ConnectWise RAT, a Remote Access Trojan.
- Persistence Tricks: The malware sets itself to run at every startup by editing Windows Registry and creating system services, making it hard to remove.
- Remote Control: The malware connects to a remote server (screenconnect.com) allowing hackers to steal data, spy on users, and move within the network.
- Real Software Used for Harm: The ConnectWise Control tool—originally made for remote tech support—is being misused for cyberattacks.
This is a clear example of how hackers blend fake emails, trusted platforms, and legitimate-looking tools to launch powerful cyberattacks. Users must always double-check links, avoid downloading unknown files, and never enter login credentials on suspicious pages.
Net Protector Cyber Security urges all users and businesses to use anti-phishing protection, endpoint security, and enable multi-factor authentication (MFA) to stay protected from such multi-layered threats.






