Ghost Tap: The Emerging NFC Exploit Fueling Global Mobile Payment Fraud

Hackers are exploiting a technique called Ghost Tap, leveraging NFCGate to steal funds via mobile payment systems like Google Pay and Apple Pay. By relaying stolen NFC data, criminals conduct fraudulent transactions worldwide without needing physical access to victim devices. This alarming development underscores the need for heightened cybersecurity measures for mobile payment platforms.
What is Ghost Tap?
- A cyberattack method using NFC technology to relay stolen tap-to-pay information from Google Pay and Apple Pay accounts.
How it Works:
- Hackers infect victims with malware to steal credit card details and credentials.
- Card details are linked to mobile payment platforms.
- NFC traffic is relayed via NFCGate to a mule, enabling global fraudulent transactions.
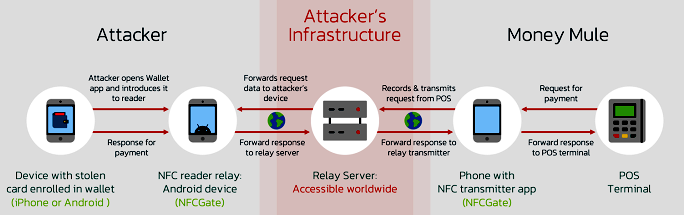
Key Techniques Used:
- Mobile banking malware for data theft (e.g., keyloggers, overlay attacks).
- Use of NFCGate to capture and relay NFC traffic.
- Fraudulent purchases conducted by mules using stolen data.
Complications for Detection:
- Transactions appear legitimate and originate from the victim's device.
- Devices can operate in airplane mode, obscuring their actual location.
- Scalability via multiple mules conducting rapid fraudulent transactions globally.
Implications:
- Financial institutions face significant challenges due to anonymous, large-scale fraud.
- Retailers struggle with detecting these sophisticated schemes.
Protective Measures:
- Implement time-based fraud detection systems on PoS terminals.
- Enhance multi-factor authentication for mobile payments.
- Monitor unusual transaction patterns, especially cross-border activities.
The rise of Ghost Tap attacks represents a serious threat to mobile payment security, with hackers exploiting NFC technology to steal funds at scale. As fraud detection systems lag behind these sophisticated methods, it is crucial for financial institutions, retailers, and users to adopt proactive cybersecurity measures. Enhanced vigilance and innovative detection mechanisms are necessary to combat this evolving fraud landscape.






