Google play store security evaded once again by "JOKER" malware
Joker was found again in some of the applications present in the Google play store.
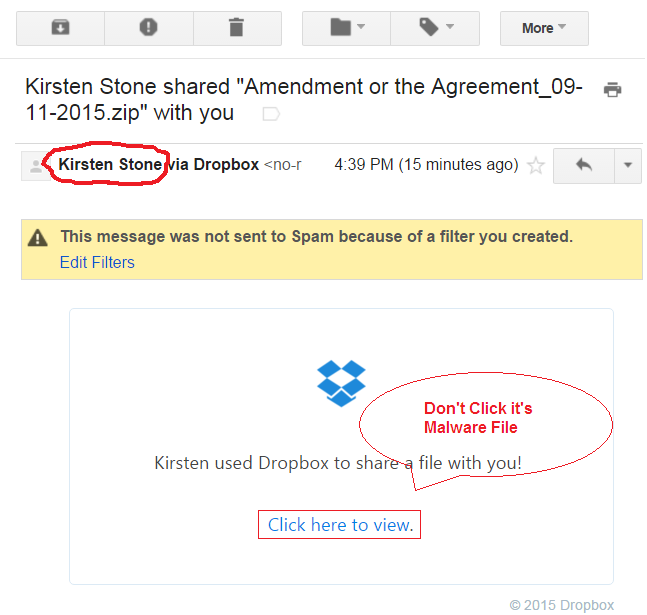
Spyware infected apps were put in the Google play store by Joker malware as it managed to evade the security features used by the store. Android applications infected with Joker malware, a spyware and premium dialer tool known as Bread, were originally designed to perform SMS fraud.
The new version of Joker found in the play store uses an all new method to trick its targets. This new method used by the android trojan is known as toll fraud which is used to trick their victims into subscribing or buying various types of content via their mobile phone bill.
Joker is now more lethal than ever before as this time it has no connection requirement to a command and control server for downloading malicious files and codes. Joker hides malicious codes and files in the application which user downloads from the play store and falls right into its trap.
Researchers have stated that the security features used by Google is not enough to stop Joker, as numerous cases of Joker uploads to the play store were found on a weekly basis.
NPAV recommends users to immediately uninstall any application can is not from a trusted source or can be infected. Users should also check their mobile and card bills for any new subscriptions and keep monitoring for the same.
Install NPAV mobile application to protect your android devices from all kinds of cyber attacks. Use NPAV and join us on a mission to secure the cyber world.






