Locky Ransomware new variant with .asasin extension

The latest variant of Locky Ransomware is released. Distributed via spam email containing infected attachments or links to malicious websites.
Once infected, it will scan your PC for .doc, .docx, .xls, .pdf etc files and encrypt them adding an .asasin extension.
After encryption, the Locky will create the Asasin.html, Asasin_[4_digit_number].html, and Asasin.bmp files ransom note in each folder.
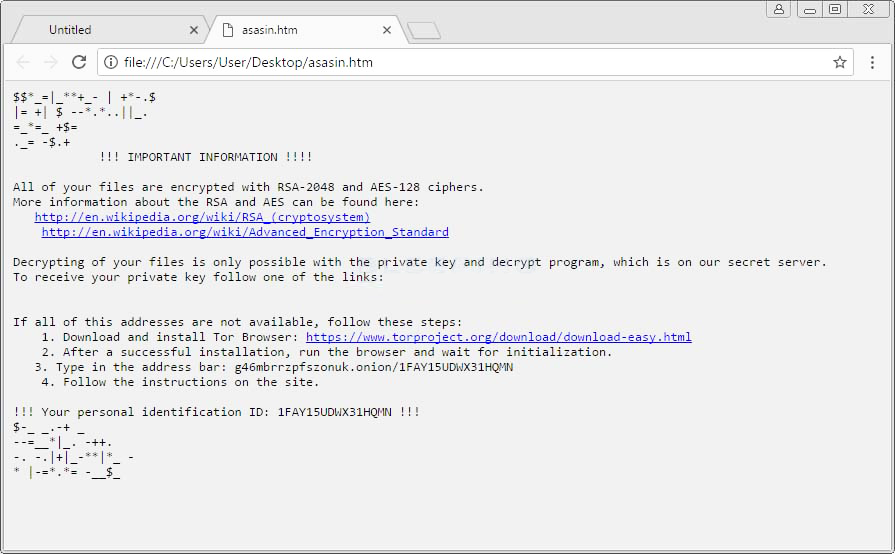
Once the user's files are encrypted a ransom note is displayed, instructing the victim to pay a fee, usually in the form of Bitcoin (BTC).
NPAV recommend that all users should be alert of spam emails.
Do not click or download attachments from suspicious or unknown mails. It is very easy for the ransomware to pretend to be a payment invoice or job application or shipping order. Also think twice before installing unverified programs and don't trust illegitimate websites.






