New Deep Ransomware

A new and active Ransomware is Deep where attackers are hacking into computers with Internet accessible Remote Desktop Services.
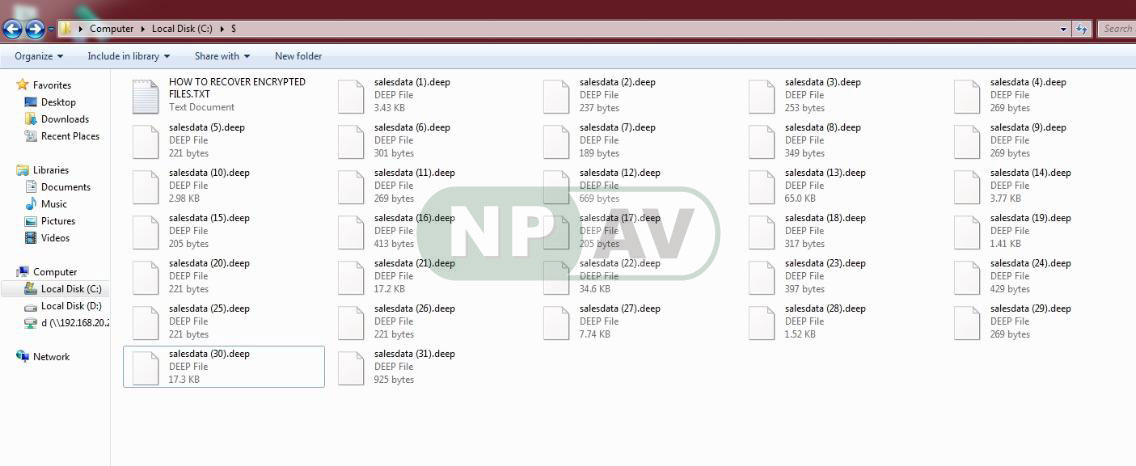
When installed, Deep will encrypt a victim’s files and append the .deep extension to the encrypted file’s name. This means that a file named sales.txt would be encrypted and renamed to sales.txt.deep as shown below.
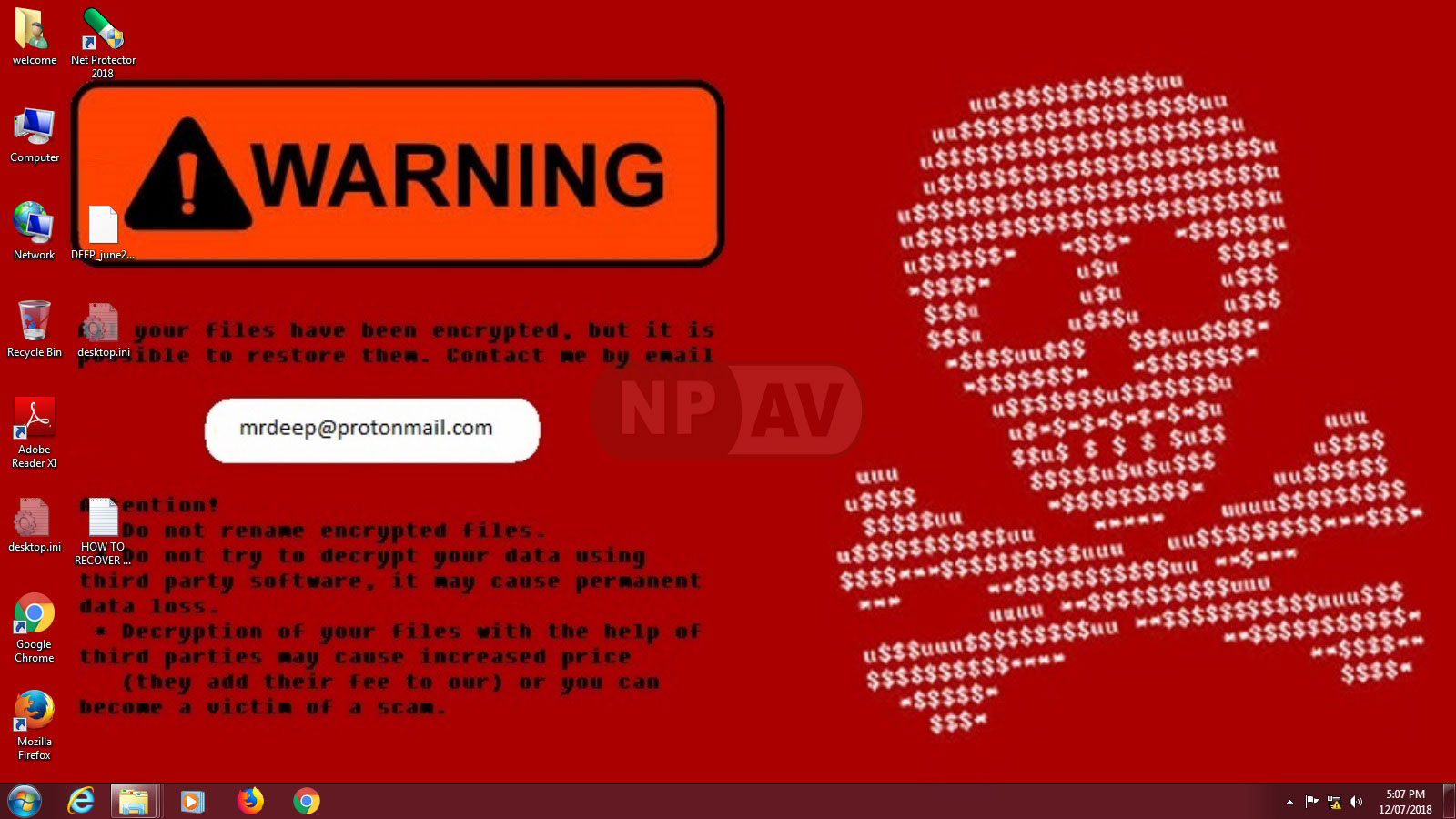
The users desktop wallpaper will be changed to Ransomware note's wallpaper as shown below
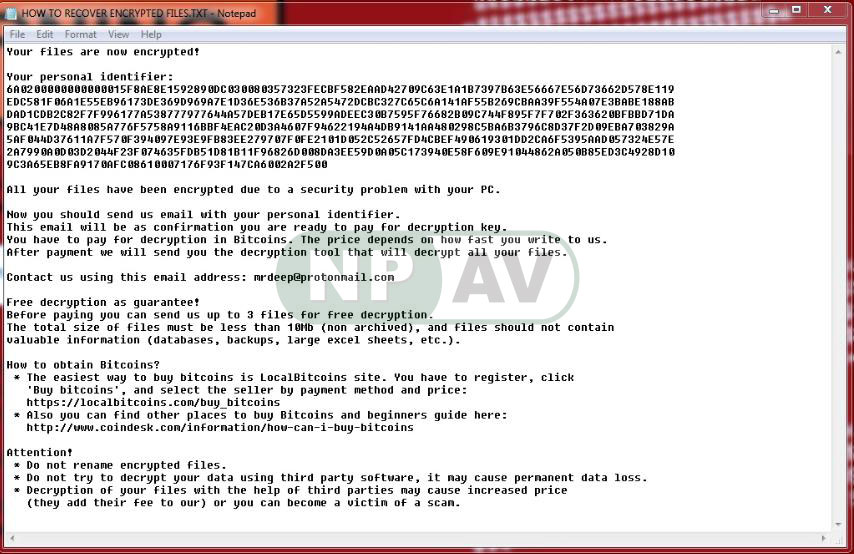
In each folder that files are encrypted, a ransom note named HOW TO RECOVER ENCRYPTED FILES.txt will also be created that contains instructions about how to make payment.
It is not possible to decrypt the Deep Ransomware. Unfortunately, at this time there is no way to decrypt files encrypted by the Deep Ransomware for free.
Ransomware Text:
Your files are now encrypted!
Your personal identifier:
6A0200000000000015F8AE8E1592890DC030080357323FECBF582EAAD42709C63
EDC581F06A1E55EB96173DE369D969A7E1D36E536B37A52A5472DCBC327C65C6A1
DAD1CDB2C82F7F996177A538777977644A57DEB17E65D5599ADEEC30B7595F7668
9BC41E7D48A8085A776F5758A9116BBF4EAC20D3A4607F94622194A4DB9141AA48
5AF044D37611A7F570F394097E93E9FB83EE279707F0FE2101D052C52657FD4CBE
2A7990A0D03D2044F23F074635FDB51D81B11F96826D008DA3EE59D0A05C17394
9C3A65EB8FA9170AFC08610007176F93F147CA6002A2F500All your files have been encrypted due to a security problem with your PC.
Now you should send us email with your personal identifier.
This email will be as confirmation you are ready to pay for decryption key.
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us.
After payment we will send you the decryption tool that will decrypt all your files.Contact us using this email address: mrdeep@protonmail.com
Free decryption as guarantee!
Before paying you can send us up to 3 files for free decryption.
The total size of files must be less than 10Mb (non archived), and files should not contain
valuable information (databases, backups, large excel sheets, etc.).How to obtain Bitcoins?
* The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click
'Buy bitcoins', and select the seller by payment method and price:
https://localbitcoins.com/buy_bitcoins
* Also you can find other places to buy Bitcoins and beginners guide here:
http://www.coindesk.com/information/how-can-i-buy-bitcoinsAttention!
* Do not rename encrypted files.
* Do not try to decrypt your data using third party software, it may cause permanent data loss.
* Decryption of your files with the help of third parties may cause increased price
(they add their fee to our) or you can become a victim of a scam.
How to protect yourself from the Deep Ransomware?
In order to protect yourself from Deep, or from any ransomware, it is important that you use good computing habits and security software. First and foremost, you should always have a reliable and tested backup of your data that can be restored in the case of an emergency, such as a ransomware attack.
As the Deep Ransomware is commonly installed via hacked Remote Desktop services, it is very important to make sure its locked down correctly. This includes making sure that no computers running remote desktop services are connected directly to the Internet. Instead place computers running remote desktop behind VPNs so that they are only accessible to those who have VPN accounts on your network.
All Users are requested to:
- Install and keep NPAV updated up-to-date.
- Make sure NPAV Data Backup is ON.
- Always use trusted and secure sites for downloading setups.






