Tips to Protect from Ransomware (CryptoLocker, CTB-Locker)

Ransomware, one of the types of threats that have been increasing in recent months. The purpose of this type of malware is to kidnap” a user’s information by encrypting it and to demand payment as a ransom. It has infected your computer, the methods used to propagate ransomware are ordinary enough, such as social engineering through email messages, therefore following simple precautions can stop you falling victim to this type of malware.
The various malware propagation campaigns based on the mass mailing of email messages with attachments. Some of the most frequently used involve ransomware like CryptoLocker, TorrentLocker or more recently CTB-Locker, which are propagated using email attachments, among other methods. Once installed on the user’s computer, this “filecoder” code will encrypt the victim’s information and demand a payment as ransom in exchange for supplying a password which will decrypt the information. If the user pays the ransom, the key will work only on their infected system, so the decryption keys cannot be used to save another person’s infected computer.
To prevent or minimize the consequences of an infection by this malware, email being the main tool in need of protection.
Don't share your email address:
The hackers collect email address, which they can find by searching on publicly accessible websites mostly from social web forums. The aim is to gather together a large number of email accounts in order to propagate malicious code, or to carry out other malicious activities like sending spam, launching unsolicited advertising campaigns, or mounting phishing attacks. Also, when you send emails to more than one address without using bcc, the messages accumulate valid email addresses, allowing cybercriminals to find such information more easily. Resending entire email chains also makes it easier to collect email addresses for malicious campaigns.
Please Check the content of the email, What you received and What you send? :
Most important is that, you have to check the content of the messages you received by email and their attachments also. Email attachment have become a very common method for propagating malware. This is one of the main means of infection by ransomware. The hacker are sending emails pretending to be from well known organization. So you have to check that it is really an email that has been sent by trusted organization. Do not directly click on the link, you have to check that, Is it a real email address, check the nevigation URL (Just move the mouse on link and check the Navigation URL on bottom of the screen). The suspicious links are basic measures to take in order to avoid falling victim to tricks that might result in infection.
Use a Net Protector to protect yourself against malicious code :
Always use the antivirus protection to protect yourself from such types of malwares family. If, by mistake or through lack of knowledge, a malicious file is downloaded or a malicious/suspicious link is clicked on, the Net Protector will prevent the malicious code from executing itself. Updated antivirus software regularly and configured with the correct settings.

Updating your software is essential for preventing more infections. Update your antivirus software regularly. it’s important to check the authenticity of the software you download and install on your computer. Although the most common method of propagating ransomware is by email, other vectors of attack may be used, such as by infecting websites or legitimate programs and apps that are downloaded frequently.
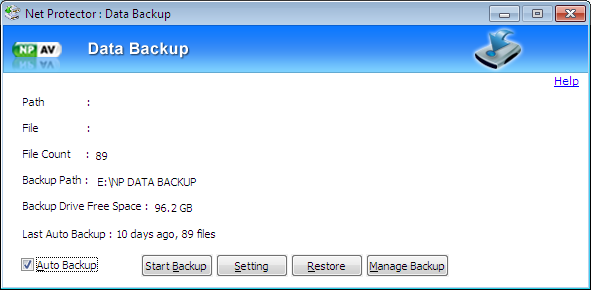
Take your important information backup on external drive :
Take your important information backup regularly on external drive. Our Net Protector Data Backup features are helpful to you in this situation. we are recommended to you that, Ignore the email messages from people you don’t know and not downloading attachments, these two methods are most important ways to avoid infection. But if your computer does become infected by ransomware, a backup is your best weapon of defense, You can restore all the Backup information from external storage.
Net Protector Data Backup Features: Click here to details..