How to monitor the Internet Traffic over the LAN ?
Net Protector Endpoint Security Provide the New Feature to Monitor the Internet Traffic over the LAN.
What is Internet Traffic Monitor ?
Internet traffic monitor is the fastest traffic manager, which find out the high bandwidth consumable PCs over the LAN. All PCs network data reports shows on the end Point Security application. How much data is uploaded and downloaded from the internet. Administrator can take action against that PCs or it can be easily restrict the internet access or usage. Very systematic graphical representation along with data statistics.
How to Start the Traffic Monitor ?
1. Open the EndPoint Security Application
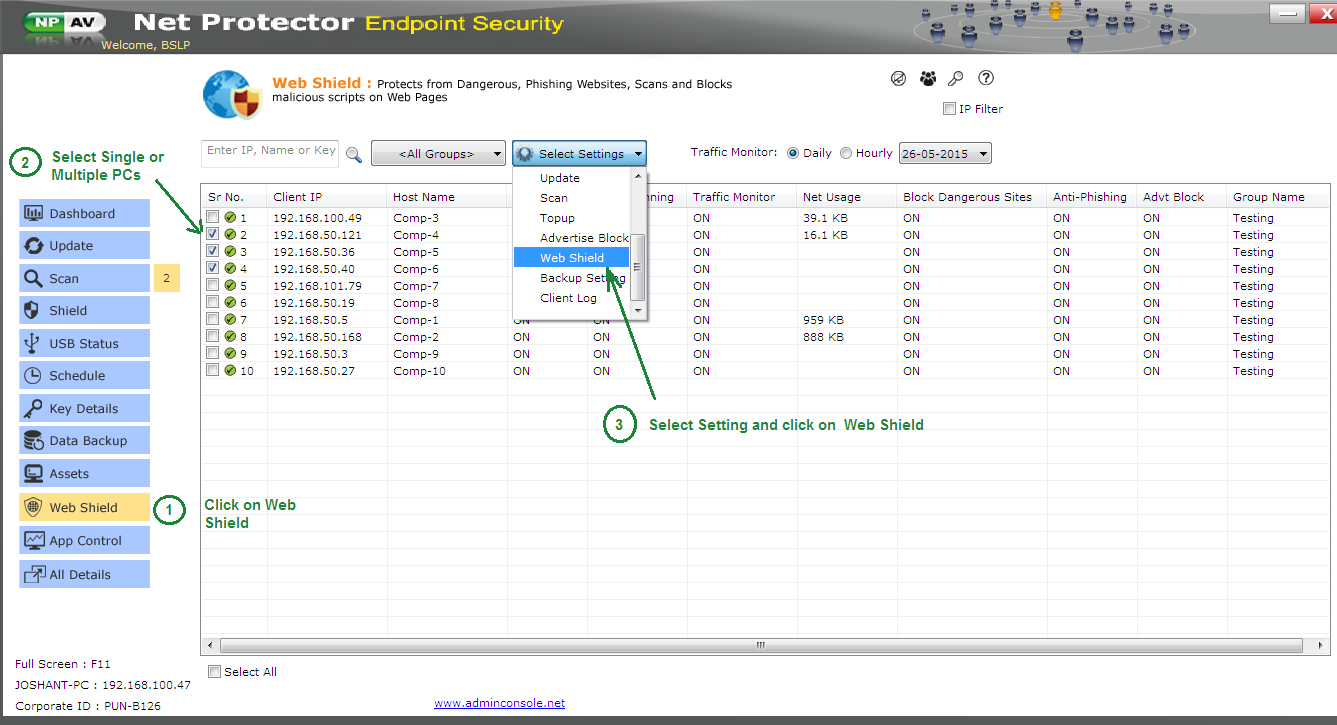
2. Go to >> Web Shield Tab
3. Select single or multiple PCs and go to setting menu
4. Select Setting >> Web Shield
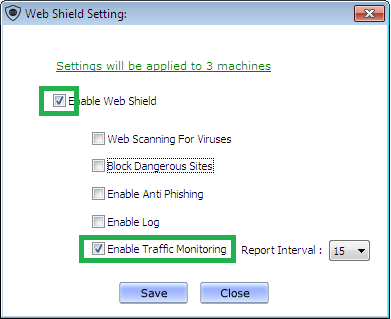
5. Click on Save button.
How to see the Report ?
Go to "Web shield" tab select any PC and right click option >> Traffic Monitor
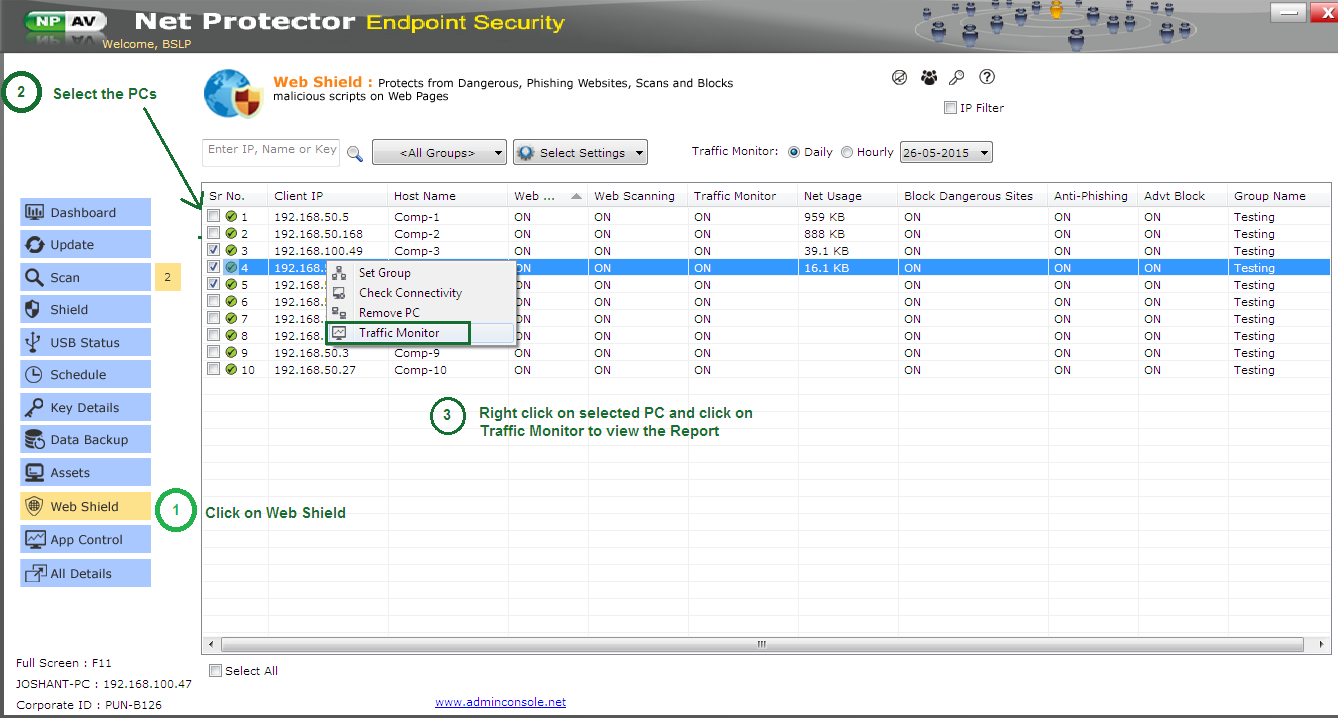
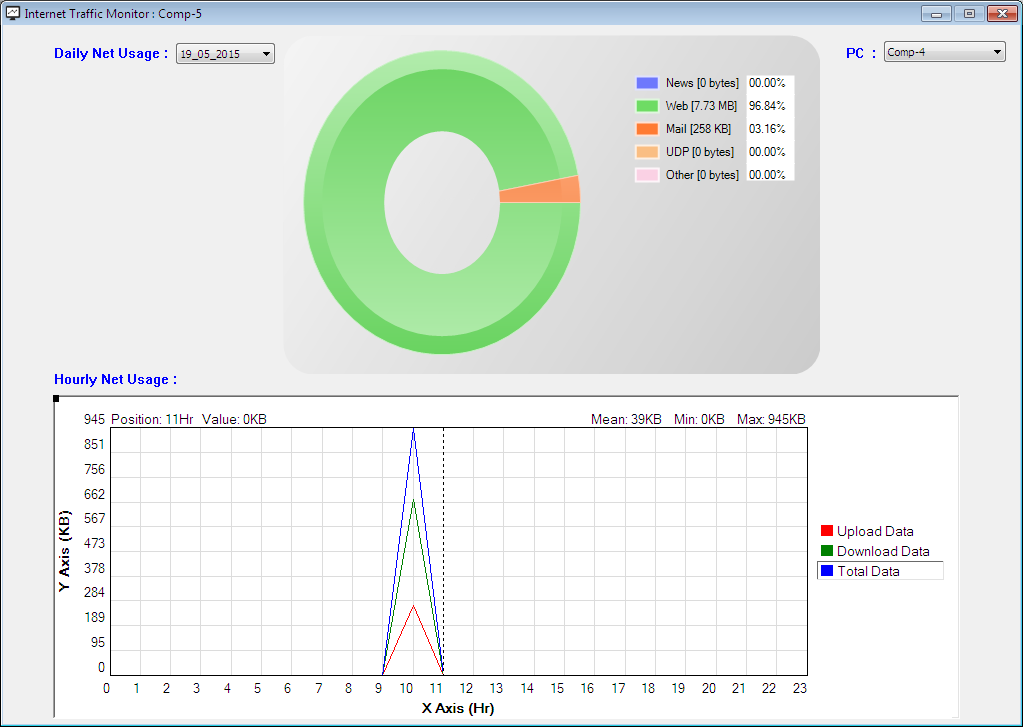
Traffic Monitor Graphs are divided into two categories :
Daily Net Usage:
Pie chart contains five protocol categories
a. News
b. Web
c. Mail
d. UDP
e. Other
Hourly Net Usage:
a. Upload Data
b. Download Data
c. Total Data