fp-1a
-
Read moreA hacker alleges stealing Huawei's source code, dev tools, scripts, and manuals in a major breach, offering them on dark web forums—echoing past espionage fears from U.S. warnings, Vodafone backdoors, and NSA hacks. Investigation ongoing amid global security risks.
-
Read moreLayerX uncovers CometJacking, exploiting Perplexity’s AI browser via malicious URLs to steal Gmail/Calendar data—tricks AI into Base64-encoded exfiltration, bypassing safeguards. Urgent call for AI security-by-design amid rising agentic threats.
-
Read moreCVE-2025-43400 enables out-of-bounds writes via malicious fonts, risking app crashes and memory corruption on macOS, iOS, and more—no active exploits yet, but RCE potential. Update to Sequoia 15.7.1 immediately for protection against untrusted files.
-
Read moreTrend Micro uncovers SORVEPOTEL, a worm-like malware exploiting WhatsApp for fast propagation on Windows systems in Brazil—phishing ZIPs lead to account bans and enterprise hits in government, tech sectors. Detect and block early to avoid spam floods.
-
Read moreA breach at Discord's third-party support vendor leaked personal info like names, emails, IP addresses, limited billing details, and scanned photo IDs for some users—no passwords or full cards affected. Discord is investigating and notifying victims; stay alert for phishing.
-
Read moreThe DPDP Act makes employee data protection crucial for India Inc. Learn about compliance, required safeguards (encryption, MFA), and the high cost of data leaks.
-
Read moreMicrosoft uncovers advanced XCSSET variant infecting Xcode projects for macOS devs—adds Firefox data exfiltration, crypto wallet clipboard swaps via AES-encrypted AppleScripts, and LaunchDaemon persistence. Mitigate with updates, Defender for Endpoint, and domain blocks.
-
Read moreMicrosoft exposes AI-driven phishing campaign targeting US organizations: attackers use AI to craft verbose, business-jargon code in SVG attachments disguised as PDFs, hiding credential-stealing payloads behind invisible dashboards and evading antivirus detection.
-
Read moreXLab exposes the AISURU botnet, a 300,000-node powerhouse driving 11.5 Tbps DDoS peaks since 2025 via Totolink firmware hacks. Led by Snow, Tom, and Forky, it features ideological Easter eggs; rivals leak evidence amid calls for takedown amid escalating threats.
-
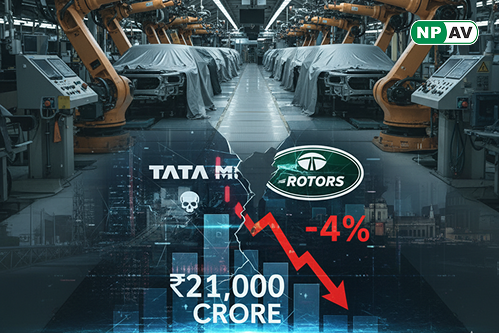
Read moreMajor cyberattack on Jaguar Land Rover (JLR) causes Tata Motors shares to drop 4% to ₹655.30; production paused until Oct 1 with ₹560 crore weekly losses, potential ₹21,000 crore damage—exceeding annual profit. Experts urge cyber insurance and resilient IT amid auto sector digital risks.