Alert ! Phishing Targeting Google Play Android Developers!

A phishing campaign targeting Android developers who are publishing their creations in Google Play, Android’s official app store. The from field in the email comes from “Play Developer Support”, with the subject “Update your Account Informations”, as you can see in the following screenshot:
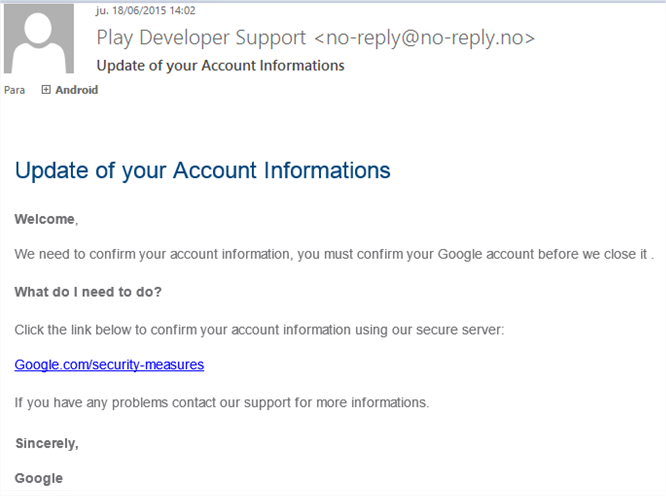
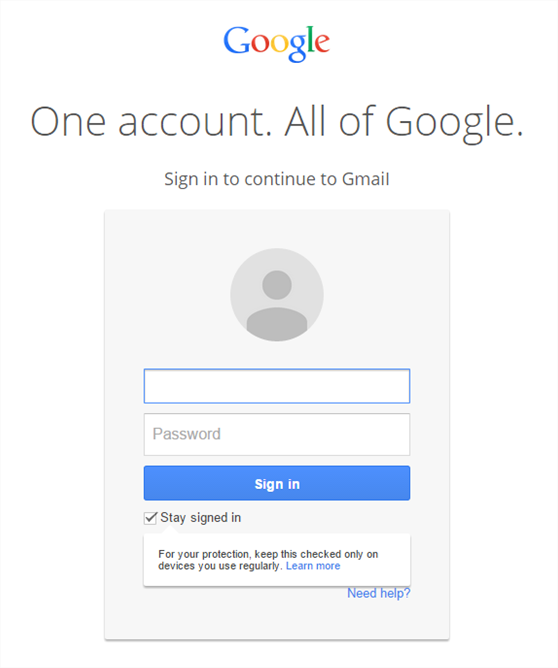
Phishing attacks are designed to steal credentials and users’ identity, that’s why they are extremely popular targeting financial entities and all kind of payment platforms’ customers. This case, however, it is different in the sense that they are not looking to syphon the victims account, the want those credentials because they can use them to spread malware through Google Play.
The most worrisome thing is how easy it would be to automate all the process for criminals. You just need to:
Phishing attacks are designed to steal credentials and users’ identity, that’s why they are extremely popular targeting financial entities and all kind of payment platforms’ customers. This case, however, it is different in the sense that they are not looking to syphon the victims account, the want those credentials because they can use them to spread malware through Google Play.
The most worrisome thing is how easy it would be to automate all the process for criminals. You just need to:
Build a crawler (there are a number of open source projects to help out in this task) to download information of all apps published in Google Play. Parse that information to obtain developers’ email addresses. Sent out a personalized phishing campaign, even the phishing page could be personalized for the specific developer so the “conversion rate” is better. As the attacker has the information from the apps published by each developer, it could be built an alert system to warn him each time a developer with a popular (millions of downloads) app has fallen in the trap.
From here, one of the easier (and unsophisticated) attacks would be to publish malicious apps using that account. Imagine that someone gets to steal the developer credentials of Candy Crush and publish Candy Crush 2 on the developer behalf…
If the attackers were skilled enough, and find a way to modify the current app of the developer without using the private key (this one cannot be obtained with the stolen credentials), they could publish an updated version of any app. In the example above, imagine that the attackers create an update of Candy Crush with a hidden Trojan in it: hundreds of millions of users would download and install it without ever suspecting they are being compromised.
Net protector Antivirus Provides a powerful Anti-phishing feature to deals with that kinds of threats while you surfing.






