Android Malware Masquerades as Popular Apps to Steal Credentials

Recent findings reveal that malicious Android apps are posing as popular apps like Google, Instagram, Snapchat, WhatsApp, and X (formerly Twitter) to steal users' credentials from compromised devices.
According to the SonicWall Capture Labs threat research team, these malware apps use recognizable icons to deceive users into installing them. Once installed, the apps request permissions for accessibility services and the deprecated device administrator API, allowing them to take control of the device and perform various malicious activities, including data theft and malware deployment.
These rogue apps connect to a command-and-control (C2) server to receive commands, enabling them to access contact lists, SMS messages, call logs, install apps, send SMS messages, open phishing pages, and control the camera flashlight. Phishing URLs mimic login pages of well-known services such as Facebook, GitHub, Instagram, LinkedIn, Microsoft, Netflix, PayPal, Proton Mail, Snapchat, Tumblr, X, WordPress, and Yahoo.
A Google spokesperson confirmed to The Hacker News that Google Play Protect, Android's built-in malware defence, automatically protects users from apps with known malware versions.
The rise in such attacks coincides with warnings from Cyfirma and Broadcom-owned Symantec about a social engineering campaign using WhatsApp to distribute new Android malware disguised as a defence-related application. Once installed, this app poses as a Contacts application, requesting permissions for SMS, Contacts, Storage, and Telephone, then hiding itself from view.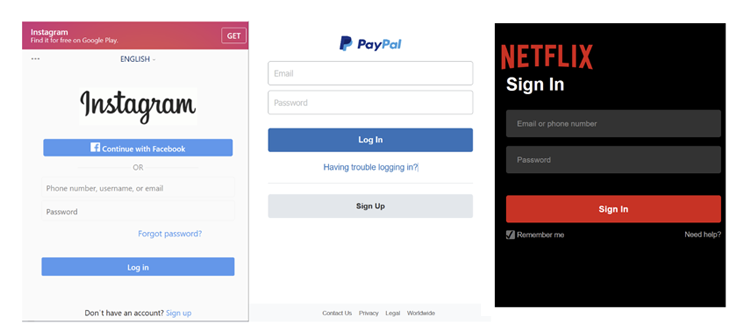
Additionally, malware campaigns are distributing Android banking trojans like Coper, which harvest sensitive information and display fake window overlays to deceive users into surrendering their credentials.
Finland's National Cyber Security Centre (NCSC-FI) recently revealed that smishing messages are being used to direct users to Android malware that steals banking data through a technique called telephone-oriented attack delivery (TOAD). Victims are urged to call a number regarding a debt collection claim and then instructed to install a supposed antivirus app, which is actually malware designed to steal online banking credentials and perform unauthorized fund transfers.
Recent months have also seen the detection of Android malware like Tambir and Dwphon, with Dwphon targeting Chinese handset makers and primarily intended for the Russian market. Kaspersky suggests that Dwphon may be a result of a supply chain attack, incorporating the infected application into the firmware.
Telemetry data from Kaspersky indicates a 32% increase in attacks on Android users by banking malware, with the number of affected users rising from 57,219 to 75,521, especially in Turkey, Saudi Arabia, Spain, Switzerland, and India. In contrast, PC banking malware attacks continue to decline, while mobile banking Trojans are becoming more prevalent in 2023.






