Beware of Email Phishing: Protect Your Inbox from Deceptive Scams

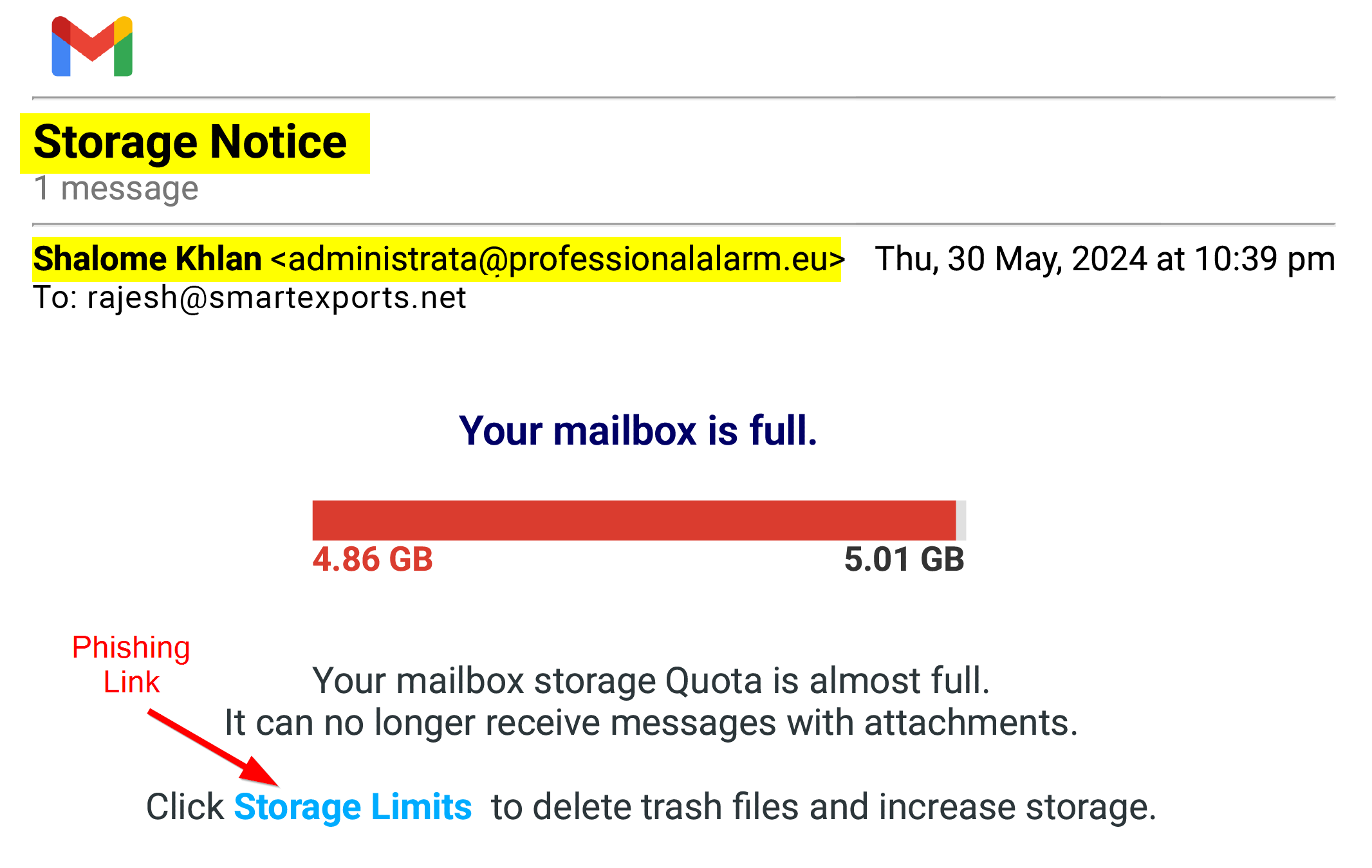
In today’s digital age, email has become an indispensable communication tool, but it has also become a prime target for cybercriminals. One of the most common and dangerous tactics they use is email phishing. A recent example that’s been making the rounds is an alarming message claiming, "Your mailbox storage quota is almost full. It can no longer receive messages with attachments. Click storage limits to delete trash files and increase storage."
At first glance, this email might seem legitimate and prompt you to take immediate action to avoid losing important messages. However, this is precisely what the attackers want – to trick you into clicking a malicious link or providing sensitive information.
What is Email Phishing?
Email phishing is a cyberattack where attackers send fraudulent messages designed to trick recipients into revealing personal information, such as passwords, credit card numbers, or other sensitive data. These emails often appear to come from reputable sources, making them difficult to distinguish from genuine communications.
How to Spot a Phishing Email
Here are some telltale signs that the email about your mailbox storage quota might be a phishing attempt:
Urgency and Threats: Phishing emails often create a sense of urgency, warning you that immediate action is required. The email about your storage quota uses this tactic to pressure you into clicking the link.
Generic Greetings: Be wary of emails that don’t address you personally. Authentic emails from your email provider usually include your name or username.
Suspicious Links: Hover over the link (without clicking) to see the URL. If it looks unfamiliar or doesn’t match the official website of your email provider, it’s likely a phishing attempt.
Grammatical Errors: Many phishing emails contain spelling mistakes or awkward phrasing. Legitimate companies typically proofread their communications carefully.
Unexpected Attachments or Requests: Be cautious of emails asking for sensitive information or containing unexpected attachments.
What to Do If You Receive a Phishing Email
Do Not Click Links: Avoid clicking on any links or downloading attachments from suspicious emails.
Verify the Source: Contact the company directly using a known, legitimate contact method to verify the authenticity of the email.
Report the Email: Most email providers have a feature to report phishing attempts. Use it to help prevent others from falling victim.
Delete the Email: Once reported, delete the phishing email from your inbox.
Protecting Yourself from Phishing Attacks
Use Anti-Phishing Software: Many antivirus programs include features to detect and block phishing attempts.
Enable Two-Factor Authentication (2FA): Adding an extra layer of security to your accounts can help prevent unauthorized access even if your password is compromised.
Keep Software Updated: Ensure your operating system, browsers, and antivirus software are up-to-date to protect against the latest threats.
Educate Yourself: Stay informed about the latest phishing techniques and share this knowledge with friends and family.
Phishing emails, like the one claiming your mailbox storage is full, are a constant threat. By staying vigilant and knowing the signs of a phishing attempt, you can protect yourself from these malicious attacks. Always think twice before clicking links in unsolicited emails, and remember, it’s better to be safe than sorry.






