Critical VMware ESXi Vulnerabilities Allow Attackers to Bypass Authentication

VMware recently disclosed three critical vulnerabilities in its ESXi hypervisor, which could allow attackers to bypass authentication mechanisms and gain unauthorized access to the system. These vulnerabilities pose significant risks to virtualized environments, necessitating immediate action from administrators.
Vulnerability Details
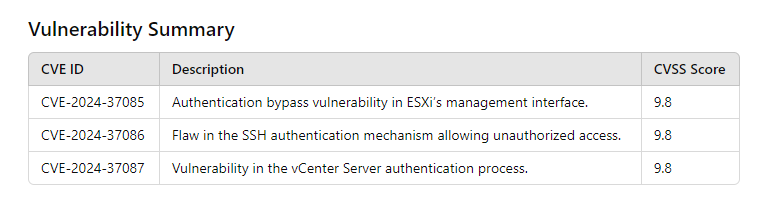
The vulnerabilities affect the authentication processes within VMware ESXi, potentially enabling unauthorized access to the system. Below are the specifics of each vulnerability:
- CVE-2024-37085: This vulnerability allows an attacker with network access to the ESXi host to bypass authentication and gain unauthorized access. The flaw lies in the improper handling of authentication tokens, which can be exploited to gain administrative privileges.
- CVE-2024-37086: Similar to CVE-2024-37085, this vulnerability permits attackers to bypass authentication by exploiting a weakness in the ESXi host’s session management, enabling them to hijack active sessions and perform unauthorized operations.
- CVE-2024-37087: This vulnerability involves a flaw in the ESXi host’s handling of authentication requests. Attackers can exploit this flaw to bypass authentication checks, gain access to sensitive information or perform administrative actions without proper authorization.
Successful exploitation of these vulnerabilities could allow attackers to gain administrative access to the ESXi host without proper authentication, leading to unauthorized control over virtual machines, data breaches, and potential disruption of services.
Mitigation and Recommended Actions
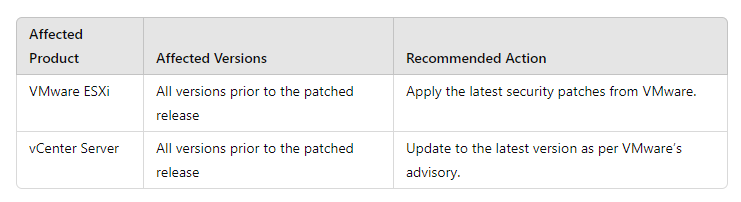
VMware has released patches to address these vulnerabilities. Administrators must apply these updates immediately to mitigate the risks. The following table summarizes the affected versions and the recommended actions:
Immediate Actions
- Patch Application: Administrators should prioritize applying the security patches provided by VMware to all affected systems.
- Network Segmentation: Isolate critical systems and limit network access to the management interfaces of VMware ESXi and vCenter Server.
- Monitoring and Logging: Implement robust monitoring and logging mechanisms to detect any unauthorized access attempts.
- Regular Audits: Conduct regular security audits and vulnerability assessments to ensure the integrity of the virtualized environment.
The discovery of these critical vulnerabilities underscores the importance of maintaining up-to-date security practices and promptly applying patches. Organizations using VMware ESXi should take immediate action to protect their virtualized environments from potential exploitation.






