DarkGate Malware Adopts AutoHotkey in Latest Cyber Attacks

The landscape of cyber threats continues to evolve, with cybercriminals constantly seeking new methods to bypass security measures. One recent example is the DarkGate malware-as-a-service (MaaS) operation, which has shifted from using AutoIt scripts to employing AutoHotkey mechanisms for its final stages of attack. This move highlights the threat actors' relentless efforts to stay ahead of detection technologies.
Evolution of DarkGate
DarkGate, a sophisticated remote access trojan (RAT), has been a persistent threat since at least 2018. Developed by an entity known as RastaFarEye, DarkGate is sold on a subscription basis to a limited clientele, estimated at around 30 customers. The malware's latest version, released in March 2024, underscores significant advancements in its delivery and evasion techniques.
Key Features of DarkGate
DarkGate is a fully-featured RAT, equipped with capabilities such as:
Command-and-Control (C2): Facilitates remote management and control over infected systems.
Rootkit Capabilities: Allows the malware to hide its presence on the infected system.
Credential Theft: Steals sensitive information such as usernames and passwords.
Keylogging and Screen Capturing: Records keystrokes and captures screen activities.
Remote Desktop Access: Enables attackers to take control of the infected machine remotely.
Shift to AutoHotkey
The transition to AutoHotkey, a scripting language less commonly used in malware, marks a significant strategic shift. According to Trellix security researcher Ernesto Fernández Provecho, this adaptation aims to evade security solutions more effectively. This is the first known instance of DarkGate utilizing AutoHotkey, emphasizing the malware's continuous evolution.
Attack Chain and Delivery Methods
The latest attack chains leveraging DarkGate exploit security vulnerabilities such as CVE-2023-36025 and CVE-2024-21412. These vulnerabilities allow the malware to bypass Microsoft Defender SmartScreen protections using phishing emails with malicious Microsoft Excel or HTML attachments.
Another observed method involves Excel files with embedded macros, which execute a Visual Basic Script (VBS) file. This VBS file invokes PowerShell commands to launch an AutoHotkey script that retrieves and decodes the DarkGate payload from a text file.
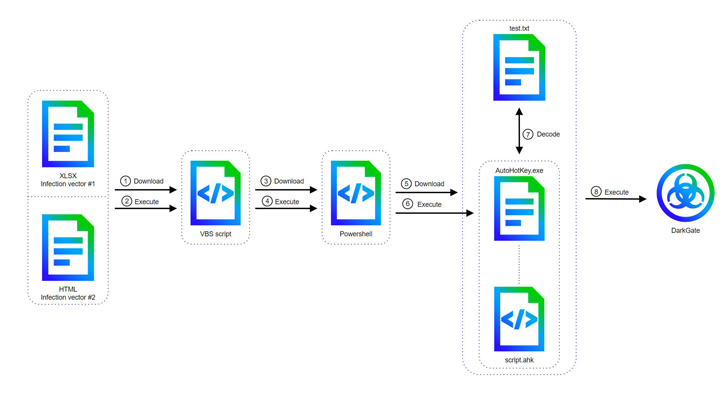
Enhancements in Version 6
The newest version of DarkGate introduces substantial upgrades:
Expanded Command Set: Now includes audio recording, mouse control, and keyboard management.
Removed Features: Excludes previous features like privilege escalation, cryptomining, and hidden virtual network computing (hVNC). This removal may be aimed at reducing detection risks or reflecting customer preferences.
Broader Implications
The emergence of DarkGate's new tactics coincides with other cybercriminal activities, such as the abuse of DocuSign. Cybercriminals are selling legitimate-looking phishing templates on underground forums, exploiting DocuSign to conduct phishing and business email compromise (BEC) scams. These emails mimic legitimate document signing requests to deceive recipients into clicking malicious links or disclosing sensitive information.
To defend against these sophisticated threats, it is crucial for organizations to adopt comprehensive cybersecurity measures:
Update and Patch Systems: Regularly update software and apply patches to mitigate known vulnerabilities.
Phishing Awareness: Train employees to recognize and respond to phishing attempts.
Advanced Security Solutions: Employ advanced threat detection and response solutions to identify and mitigate malicious activities.
Regular Audits: Conduct frequent security audits to identify and address potential weaknesses in the infrastructure.
The continuous adaptation of malware like DarkGate underscores the dynamic nature of cyber threats. By staying informed and implementing robust security practices, organizations can better protect themselves against evolving cyber risks.






