Gophish Framework Exploited in Phishing Campaigns to Deploy DCRat and PowerRAT

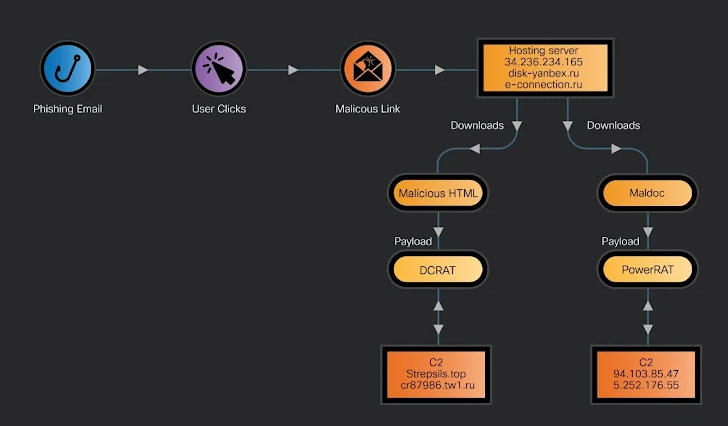
A new phishing campaign has been uncovered targeting Russian-speaking users, leveraging the Gophish framework to deliver two remote access trojans (RATs)—DarkCrystal RAT (DCRat) and a newly identified malware, PowerRAT. The campaign exploits phishing emails, malicious documents, and HTML pages to initiate infection chains, resulting in system compromise and data exfiltration.
- Gophish framework: Open-source phishing toolkit used for launching email campaigns, here repurposed by threat actors for malicious attacks.
- Target Audience: Primarily Russian-speaking users, with phishing content disguised as links to Yandex Disk and VK social networks.
- Infection Methods: Attack chains include malicious Microsoft Word documents or HTML files embedded with JavaScript to execute DCRat or PowerRAT payloads.
- PowerRAT functionality: Performs system reconnaissance, collects data, and executes PowerShell scripts based on instructions from the Command and Control (C2) server.
- DCRat capabilities: Modular RAT with the ability to steal sensitive data, capture keystrokes, and provide remote access to compromised machines.
- Persistence Mechanism: Both RATs establish persistence through Windows tasks and C2 server communication.
- Recent Trends: Threat actors are increasingly embedding malicious payloads within virtual hard disk (VHD) files to evade detection by email security systems.
The use of open-source tools like Gophish in sophisticated phishing campaigns underscores the evolving tactics threat actors are adopting to compromise systems. By deploying Remote Access Trojans such as DCRat and PowerRAT, cybercriminals can gain unauthorized access to sensitive data and further infiltrate networks. It's crucial for organizations and individuals to remain vigilant by implementing strong email security practices, regularly updating software, and educating users on how to identify and avoid phishing attacks to mitigate the risk of malware infections.






