Hackers Use New BitM Attack to Steal User Sessions in Seconds

A dangerous new cyberattack method called Browser-in-the-Middle (BitM) is allowing hackers to steal user sessions within seconds—completely bypassing Multi-Factor Authentication (MFA). This technique tricks users into logging in through an attacker-controlled browser, giving hackers full access to their accounts.
How the BitM Attack Works
BitM attacks take advantage of web browser functions to hijack authenticated sessions.
- Fake Browsing Experience: Victims click on a phishing link and are unknowingly redirected to an attacker-controlled browser.
- Credential & MFA Theft: Users enter their credentials and complete MFA, believing they are on a secure site.
- Session Hijacking: The hacker captures the authentication token from the browser and uses it to access the victim’s account without needing their password again.
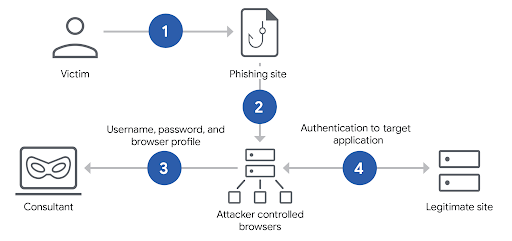
Key Dangers of BitM Attacks
- Bypasses MFA: Since the attack steals session tokens, even two-factor authentication (2FA) cannot stop hackers from logging in.
- Targets Cloud Services & Corporate Networks: Attackers can use stolen sessions to infiltrate company networks, steal data, and escalate privileges.
- Fast & Scalable: BitM attacks can be deployed quickly, making them a major threat to businesses and individuals alike.
BitM attacks are a growing cybersecurity threat that bypasses traditional security measures, including MFA. Organizations must adopt strong authentication methods, device-bound credentials, and advanced monitoring tools to prevent hackers from stealing sensitive data.
Cyber threats are evolving—stay protected with Net Protector Cyber Security.






