Impersonator of the WannaCry virus targets Russian "Enlisted" FPS players
.png)
The Enlisted multiplayer first-person shooter is the target of a ransomware operation that spreads trojanized versions of the game to Russian gamers through a bogus website.
Given that the game is free, threat actors may easily download the publisher's installer, change it, and use it to disseminate malicious payloads to unwary consumers.
Between 500,000 and one million gamers actively participate in Enlisted, a legitimate game released by Gaijin Entertainment in 2021.
Using the malicious installer (Cyble)
The malware that comes with the installation of the game poses as the third major iteration of the infamous WannaCry ransomware, even using the .wncry file extension on encrypted data.
recruited by ransomware The new "WannaCry" variety is said to be built on the open-source "Crypter" Python locker, which was obviously created for instructional purposes, according to Cyble's researchers who examined the strain.
It should be noted that this is not the first time someone has tried to mimic WannaCry; most likely, this was done to terrify victims and get a rapid ransom payment.
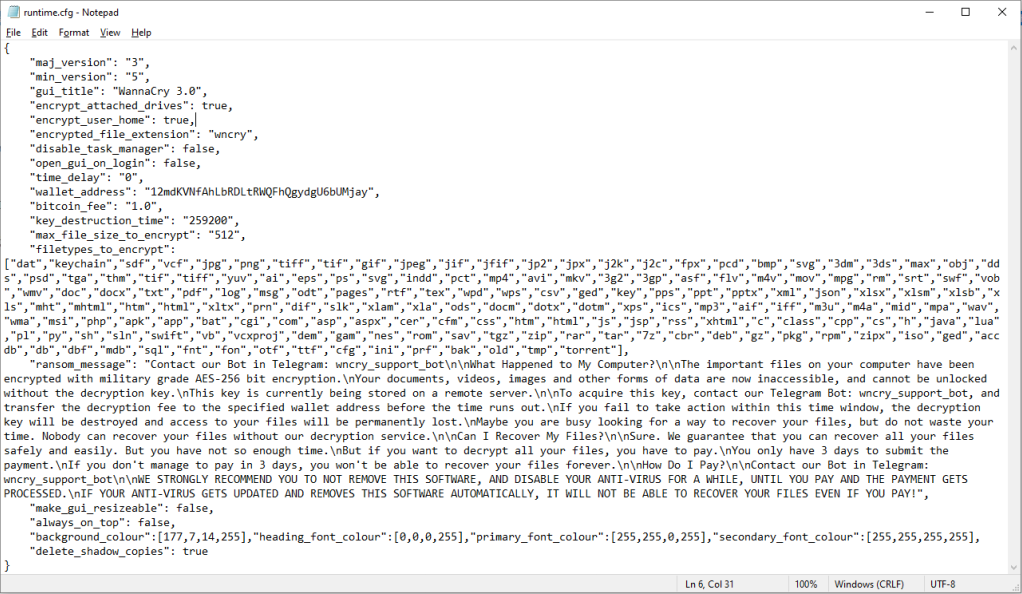
Configuration file for ransomware (Cyble)
Enlisted_beta-v1.0.3.115.exe, the installer downloaded from the bogus website, when opened drops two executable files on the user's disc: "ENLIST1" (the game itself) and "enlisted" (the Python ransomware launcher).
The JSON configuration file is then parsed to identify the parameters of the attack, including the file types that will be targeted, the directories to be skipped, the ransom note to be generated, the wallet address to which the ransom will be sent, and more.
The Crypter ransomware then looks for a "key.txt" file to utilise in the encryption process in the working directory, and if it doesn't find one, it creates one.
Each locked file receives the ".wncry" filename extension and is encrypted using the AES-256 technique.
It's interesting that the ransomware doesn't try to kill processes or halt services, which is common practice in contemporary lockers.
However, it employs the conventional tactic of wiping out Windows' shadow copies in order to hinder simple data restoration.
The ransomware displays the ransom letter on a special GUI programme after the encryption process is complete, allowing the victim three days to heed the demands.
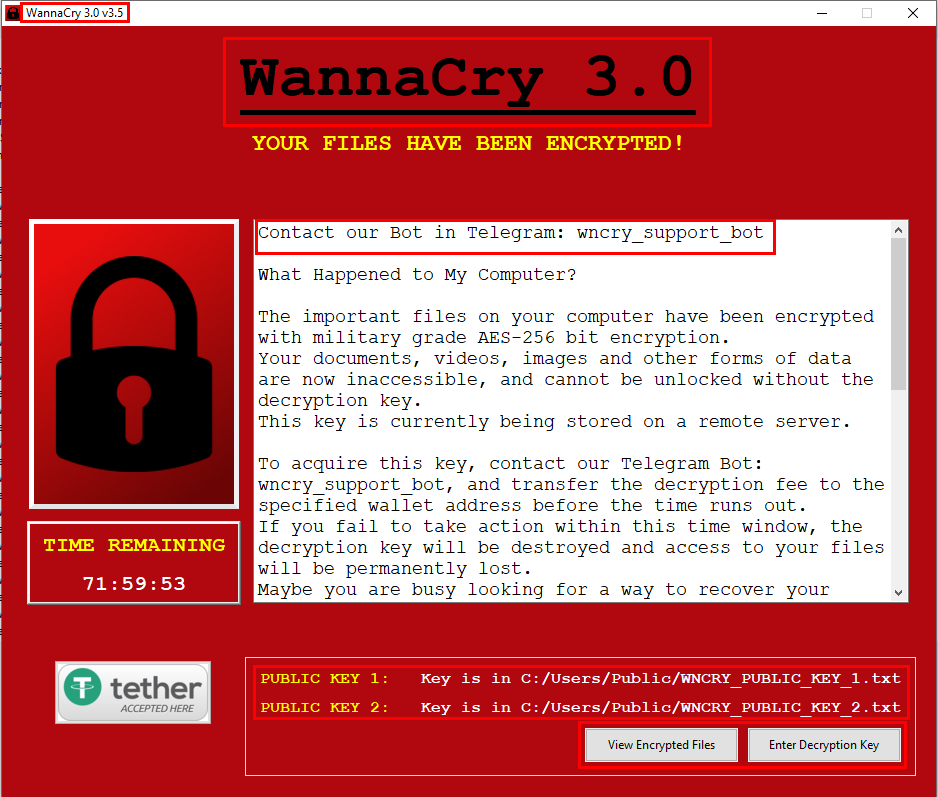
The GUI-based ransomware note (Cyble)
Even if the victim's antivirus software prevents the launch of the GUI-based ransom note, the threat actors nevertheless manage to convey their message by altering the background image of the victim.
Instead of using a Tor site or giving the victims access to a secure chat link, the attackers communicate with the victims through a Telegram bot.
Enlisted is one of the investigated alternatives as a result of national bans on popular FPS games in Russia, which have prompted local gamers to find elsewhere for enjoyment.
Threat actors seem to have seized this chance, and it's not improbable that they will make more fictitious websites for games with Russian localization.
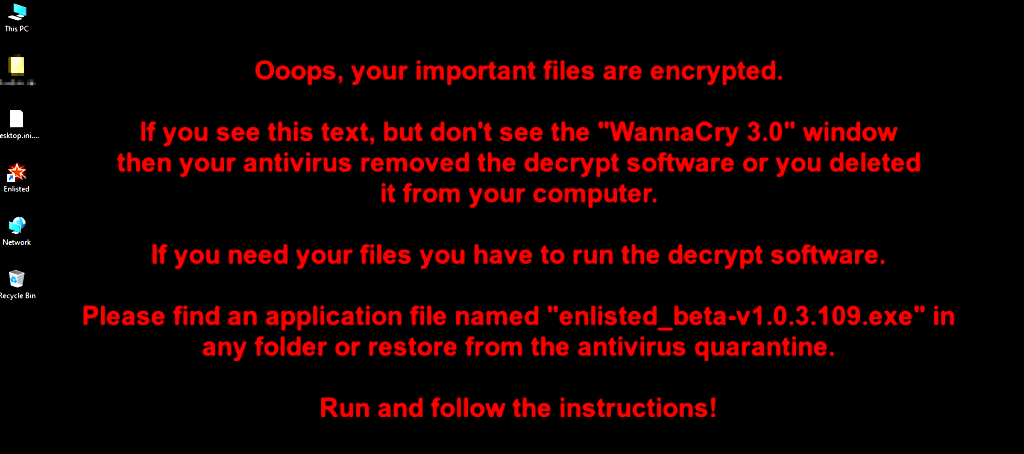
Ransome note to user on the background screen (Cyble)
The attackers use a Telegram bot for communications with the victim instead of using Tor or providing any secure chat link.
It seems that the attackers have jumped on this opportunity, and most probably they will create new fake sites for similar games in Russia or anywhere else.
- Other (43)
- Ransomware (179)
- Events and News (28)
- Features (45)
- Security (502)
- Tips (83)
- Google (43)
- Achievements (12)
- Products (37)
- Activation (7)
- Dealers (1)
- Bank Phishing (58)
- Malware Alerts (289)
- Cyber Attack (374)
- Data Backup (15)
- Data Breach (216)
- Phishing (187)
- Securty Tips (9)
- Browser Hijack (30)
- Adware (15)
- Email And Password (88)
- Android Security (95)
- Knoweldgebase (37)
- Botnet (20)
- Updates (9)
- Alert (72)
- Hacking (85)
- Social Media (10)
- vulnerability (123)
- Hacker (96)
- Spyware (18)
- Windows (23)
- Microsoft (43)
- Uber (1)
- YouTube (4)
- Trojan (7)
- Website hacks (15)
- Paytm (1)
- Credit card scam (4)
- Telegram (6)
- RAT (12)
- Bug (4)
- Twitter (3)
- Facebook (12)
- Banking Trojan (15)
- Mozilla (2)
- COVID-19 (5)
- Instagram (4)
- NPAV Announcement (17)
- IoT Security (3)
- Deals and Offers (2)
- Cloud Security (12)
- Offers (5)
- Gaming (1)
- FireFox (2)
- LinkedIn (3)
- Amazon (5)
- DMart (1)
- Payment Risk (5)
- Occasion (3)
- firewall (4)
- Cloud malware (3)
- Cloud storage (2)
- Financial fraud (106)
- Impersonation phishing (1)
- DDoS (11)
- Smishing (2)
- Whale (0)
- Whale phishing (4)
- WINRAR (3)
- ZIP (2)
- Fraud Protector (93)
-
Mobile Frauds
(69)
- WhatsApp (19)
- AI (36)






