New C# Ransomware Compiles itself at Runtime

A new in-development ransomware was discovered that has an interesting characteristic.
Instead of the distributed executable performing the ransomware functionality, the executables compiles an embedded encrypted C# program at runtime and launches it directly into memory.
This ransomware contains an encrypted string that is embedded into the dropper.
The string is then decrypted using an included decryption key.
Now the source code for the ransomware executable has been decrypted, the decrypted code is sent to another function that compiles it using the CSharpCodeProvider class and launches it directly into memory.
This method is probably being used to prevent the dropper from being detected by security software as any malicious behavior is hidden inside the encrypted string.
As for the ransomware itself, other than it saving the decryption key and IV to a file on the desktop, it is fully functional. Therefore, it wouldn't be surprising to see the ransomware being distributed at some point.
When executed, it will encrypt the files on the victim's computer and rename the files using the template sequre@tuta.io_[hex]. For example, a file called 11.jpg would be encrypted and renamed to sequre@tuta.io_31312E6A7067 .
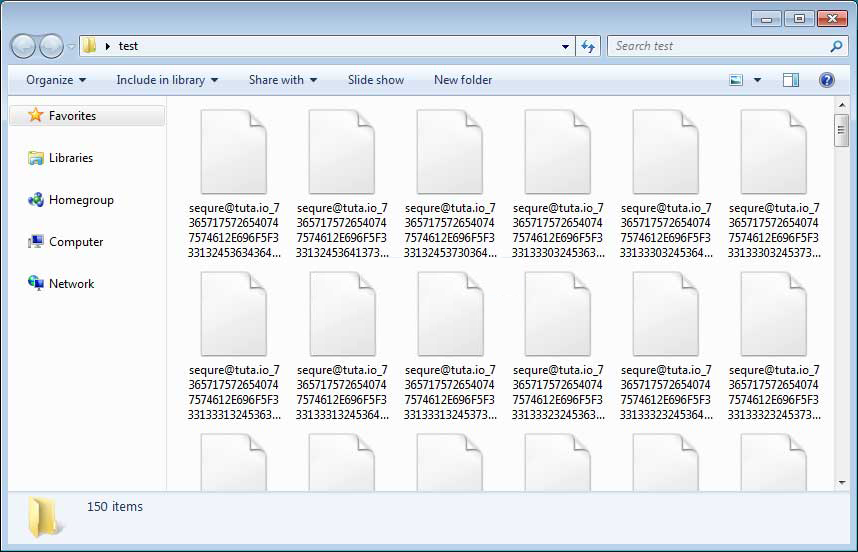
In each folder that is scanned, a ransom note named HOW DECRIPT FILES.hta is created, which provides payment instructions as shown below.
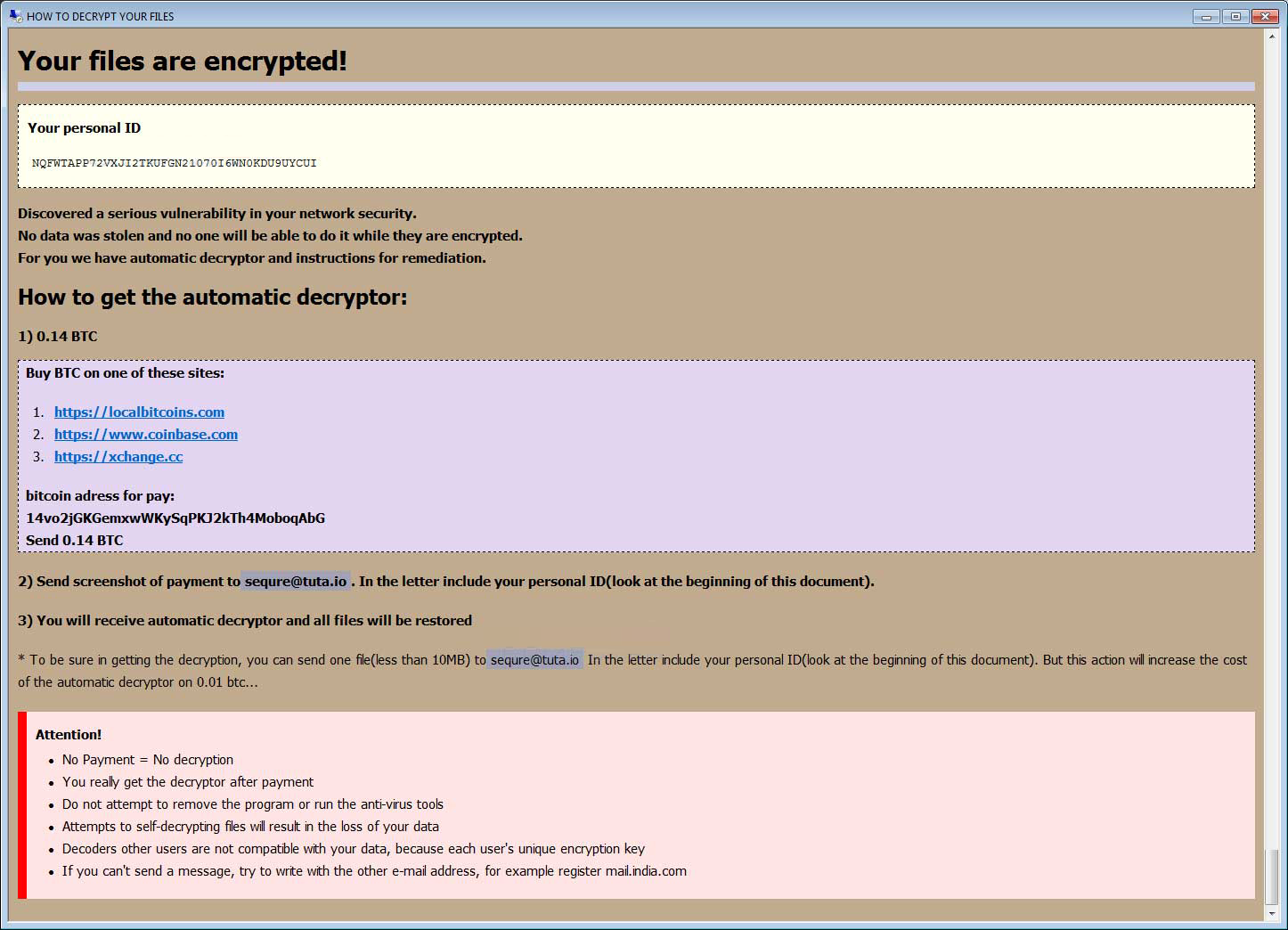
While this ransomware is still in development, it does use an interesting feature that we have not seen in ransomware before. This goes to show how attackers continue to try and think up new ways to bypass security programs that protect your computer.
All Users are requested to:
- Install and keep NPAV updated up-to-date.
- Make sure NPAV Data Backup is ON.
- Always use trusted and secure sites for downloading setups.






