New Malware Campaign Locks Browser in Kiosk Mode to Steal Google Credentials

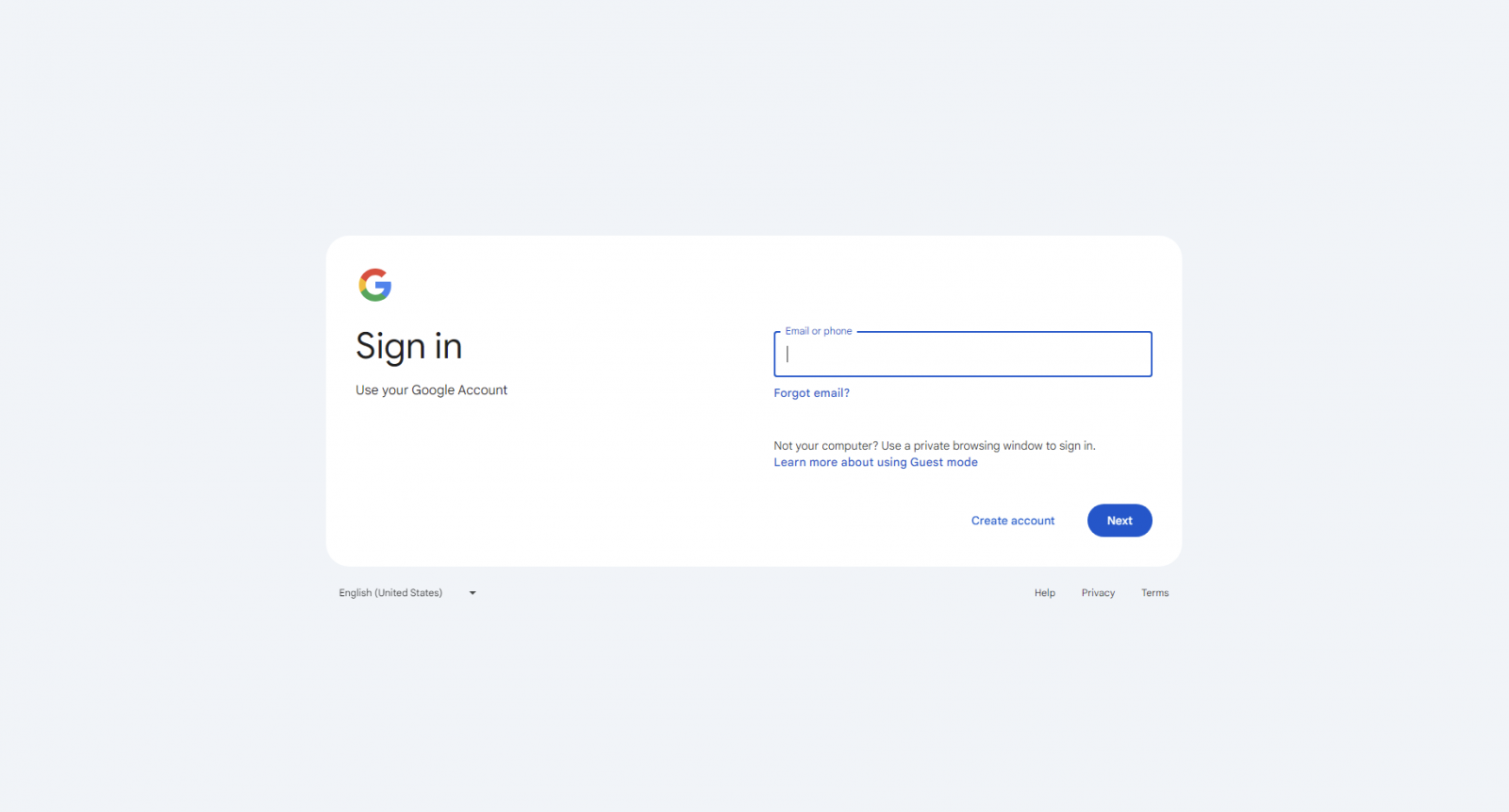
A new malware campaign has been uncovered, which uses a unique tactic to lock users' browsers in kiosk mode, forcing them to enter their Google credentials. The StealC information-stealing malware is behind this attack, and it captures the credentials to send them to cybercriminals.
Browser Lockdown in Kiosk Mode:
-
- Kiosk mode is typically used to limit user interaction in public terminals or demos. In this case, the malware abuses kiosk mode to trap the user on Google’s login page, making it appear as if there’s no other way to escape except by entering credentials.
- The malware blocks the "ESC" and "F11" keys, preventing the user from easily exiting the mode.
Credentials Theft via StealC Malware:
-
- After tricking the user into entering their Google credentials to "unlock" their computer, the StealC malware steals these credentials from the browser's credential store and sends them to attackers.
- This malware has been active since 2023 and is designed to steal sensitive information across various platforms.
- After tricking the user into entering their Google credentials to "unlock" their computer, the StealC malware steals these credentials from the browser's credential store and sends them to attackers.
Amadey Malware Loader Utilization:
-
- The malware campaign is linked to the Amadey malware loader, first identified in 2018. Amadey is responsible for launching an AutoIt script that activates kiosk mode and forces the victim to enter their credentials.
- Amadey’s loader restricts user actions and directs them to a Google password change page, making the deception seem legitimate.
Recommendations to Escape Kiosk Mode:
-
- If trapped in kiosk mode, users are advised to avoid entering any credentials. They can try:
- Alt + F4 to close the browser.
- Ctrl + Shift + Esc to open the Task Manager and end the browser process.
- Ctrl + Alt + Delete to access system controls.
- Alt + Tab to switch between open applications.
- If these don’t work, force shutting down the computer or using taskkill from the command prompt can terminate the browser session.
- If trapped in kiosk mode, users are advised to avoid entering any credentials. They can try:
Full Antivirus Scan Post-Reboot:
-
- After escaping, users should reboot the system in Safe Mode, run a full antivirus scan, and remove any malware to prevent further infections.
- Spontaneous kiosk mode launches are a sign of malware infection and should not be ignored.
This malware campaign takes an innovative approach to steal credentials by locking victims in kiosk mode and pushing them to enter sensitive information out of frustration. By abusing common browser functionalities, cybercriminals make it harder for users to detect and avoid the attack. Net Protector Antivirus users are advised to stay alert, never enter credentials under suspicious circumstances, and perform regular system scans to ensure they remain protected.






