Petya Ransomware arrives via Dropbox as a Resume.

Petya Ransomware arrives via Dropbox as a Resume.
Victims receive an email tailored to look and read like a business-related resume from an applicant seeking a position in a company. It would present users with a hyperlink to a Dropbox storage location, which supposedly would let the user download said applicant’s CV.
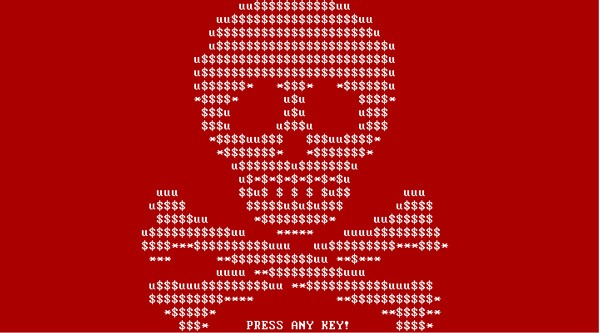
Once executed, Petya overwrites the MBR of the hard drive, causing Windows to crash and display a blue screen. Should the user try to reboot his PC, the modified MBR will prevent him from loading Windows normally and instead greet him with an ASCII skull and an ultimatum: pay up with a certain amount of bitcoins or lose access to your files and computer.
The edited MBR also disallows restarting in Safe Mode.
Comment(s)
Categories
- Other (43)
- Ransomware (179)
- Events and News (28)
- Features (45)
- Security (502)
- Tips (83)
- Google (43)
- Achievements (12)
- Products (37)
- Activation (7)
- Dealers (1)
- Bank Phishing (58)
- Malware Alerts (289)
- Cyber Attack (374)
- Data Backup (15)
- Data Breach (216)
- Phishing (187)
- Securty Tips (9)
- Browser Hijack (30)
- Adware (15)
- Email And Password (88)
- Android Security (95)
- Knoweldgebase (37)
- Botnet (20)
- Updates (9)
- Alert (72)
- Hacking (85)
- Social Media (10)
- vulnerability (123)
- Hacker (96)
- Spyware (18)
- Windows (23)
- Microsoft (43)
- Uber (1)
- YouTube (4)
- Trojan (7)
- Website hacks (15)
- Paytm (1)
- Credit card scam (4)
- Telegram (6)
- RAT (12)
- Bug (4)
- Twitter (3)
- Facebook (12)
- Banking Trojan (15)
- Mozilla (2)
- COVID-19 (5)
- Instagram (4)
- NPAV Announcement (17)
- IoT Security (3)
- Deals and Offers (2)
- Cloud Security (12)
- Offers (5)
- Gaming (1)
- FireFox (2)
- LinkedIn (3)
- Amazon (5)
- DMart (1)
- Payment Risk (5)
- Occasion (3)
- firewall (4)
- Cloud malware (3)
- Cloud storage (2)
- Financial fraud (106)
- Impersonation phishing (1)
- DDoS (11)
- Smishing (2)
- Whale (0)
- Whale phishing (4)
- WINRAR (3)
- ZIP (2)
- Fraud Protector (93)
-
Mobile Frauds
(69)
- WhatsApp (19)
- AI (36)
Recent Posts