RomCom Exploits Zero-Day Firefox and Windows Flaws in Sophisticated Cyberattacks

A Russia-aligned cybercrime group, RomCom, has leveraged two zero-day vulnerabilities in Firefox and Windows to deploy its backdoor malware, RomCom RAT, in a series of sophisticated attacks. These vulnerabilities allow remote code execution with no user interaction, escalating the threat posed by this group in both espionage and cybercrime operations.
- RomCom exploits two critical zero-day vulnerabilities:
- CVE-2024-9680 (Firefox) – A use-after-free flaw in Firefox's animation component, patched in October 2024.
- CVE-2024-49039 (Windows) – A privilege escalation vulnerability in the Windows Task Scheduler, patched in November 2024. - RomCom RAT, a powerful malware, is used to execute commands and deploy additional malicious modules.
- The attack chain involves a fake website hosting the malicious payload, exploiting the Firefox flaw to trigger code execution and downloading RomCom RAT.
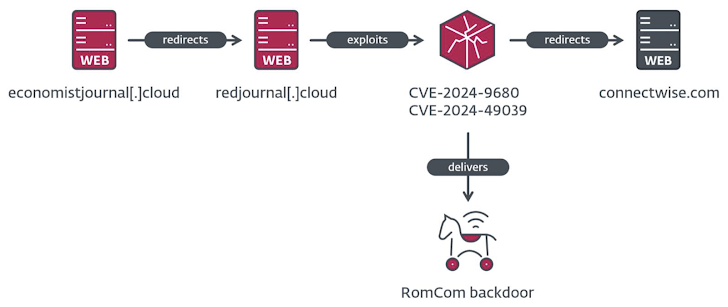
- The exploit involves a "no user interaction" attack, making it a highly sophisticated method for delivering malware.
- The exploitation of these zero-days shows RomCom’s increasing ability to create stealthy, effective cyberattacks.
- Victims primarily located in Europe and North America, highlighting the international reach of the attacks.
RomCom’s use of two zero-day vulnerabilities in Firefox and Windows demonstrates the group’s evolving sophistication and ability to exploit unpatched flaws for cyber espionage and crime. These attacks, which require no user interaction, underline the growing need for cybersecurity vigilance, including timely patching and advanced threat monitoring, to protect against such highly targeted, stealthy intrusions. Net Protector Cyber Security stands firm in helping businesses safeguard against these evolving threats.






