SteelFox Malware Exploits Vulnerable Driver to Hijack Windows PCs for Crypto Mining and Data Theft

The newly discovered SteelFox malware leverages a vulnerable driver to escalate privileges, enabling it to steal sensitive data and mine cryptocurrency on Windows machines. Distributed through cracked software on forums and torrent sites, SteelFox presents significant risks to users of popular programs like AutoCAD, JetBrains, and Foxit PDF Editor.
- Distribution Channels: SteelFox is spread via torrent trackers and online forums as cracked tools for legitimate software activation.
- Privilege Escalation: Uses the “bring your own vulnerable driver” method with WinRing0.sys to gain SYSTEM-level privileges.
- Multi-Faceted Attack: Combines cryptocurrency mining with data theft, targeting credit card data, browsing history, and other information.
- Browser Data Extraction: Retrieves sensitive details from 13 browsers, including saved credit card info and RDP connection data.
- Advanced Stealth: Hides command-and-control (C2) domain via Google Public DNS and DNS over HTTPS (DoH), making detection challenging.
- Global Reach: Primarily impacts users in Brazil, China, Russia, Mexico, and other regions, focusing on commonly cracked applications.
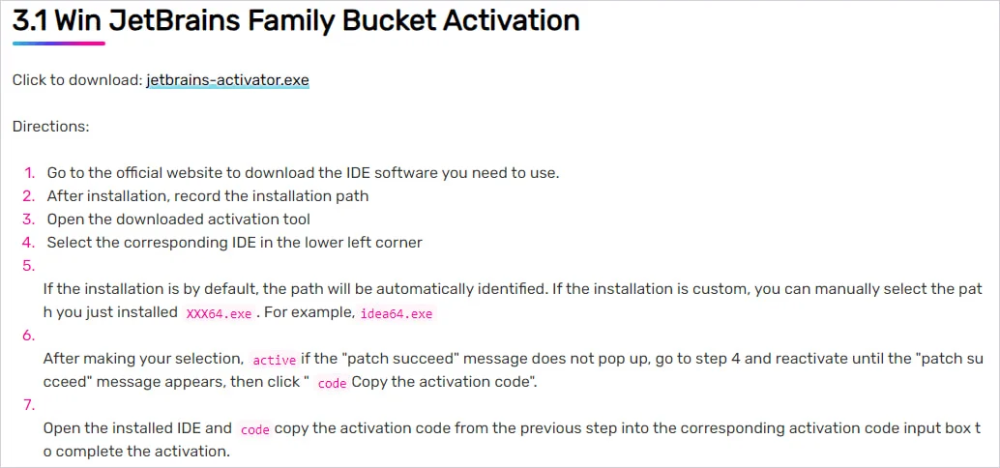
SteelFox is an advanced, multi-functional malware that combines cryptomining with data theft by exploiting a known vulnerability in Windows drivers. Users should exercise caution when downloading cracked software and maintain updated security solutions to defend against this rapidly spreading threat.
Comment(s)






