Understanding Cicada3301 Ransomware: A New Threat Targeting VMware ESXi Systems

The cyber threat landscape continues to evolve, with new ransomware-as-a-service (RaaS) operations emerging to exploit vulnerabilities and target businesses worldwide. One of the latest threats making headlines is the Cicada3301 ransomware, which has already victimized 19 companies and is quickly gaining notoriety. This blog will delve into the key details of this ransomware operation, its tactics, and how organizations can protect themselves.
The Origin of Cicada3301
Cicada3301 is named after a mysterious online game from 2012-2014 that involved complex cryptographic puzzles. Despite sharing a name and logo, there is no connection between the legitimate project and this malicious operation. The original Cicada3301 project has condemned the ransomware operators' actions.
The ransomware operation began promoting itself on June 29, 2024, through the RAMP cybercrime forum, although there is evidence of attacks as early as June 6. The gang initially operated independently before attempting to recruit affiliates.
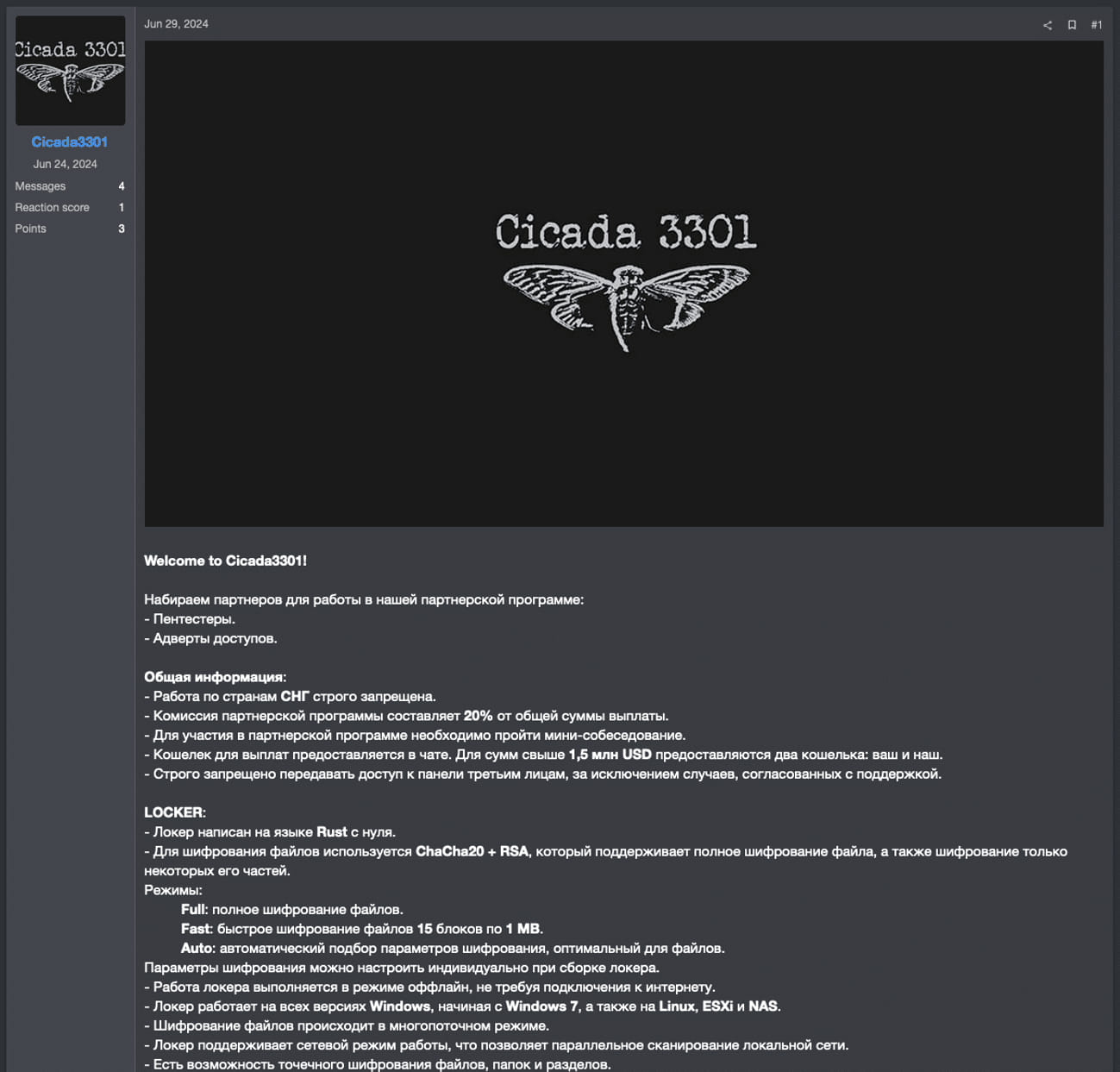
Double-Extortion Tactics
Like many other ransomware groups, Cicada3301 employs double-extortion tactics. This means that the threat actors breach corporate networks, steal sensitive data, and then encrypt devices. Victims are then coerced into paying a ransom to avoid data leaks and regain access to their systems.
The group operates a data leak site, which is part of their extortion strategy. If the ransom is not paid, they threaten to release the stolen data publicly, causing significant reputational and financial damage to the affected organization.
Technical Analysis and Links to ALPHV/BlackCat
An analysis by cybersecurity firm Truesec has revealed significant overlaps between Cicada3301 and the notorious ALPHV/BlackCat ransomware, suggesting a possible rebrand or a fork created by former members of ALPHV's core team. Some of the similarities include:
- Both ransomware strains are written in Rust, a programming language favored for its security and performance.
- Both use the ChaCha20 encryption algorithm, known for its speed and efficiency.
- Both employ similar commands to shut down virtual machines and wipe snapshots before encryption.
- Both use intermittent encryption for larger files, which can make recovery even more challenging.
ALPHV was known for its exit scam in March 2024, where it falsely claimed to have been taken down by the FBI after stealing $22 million from one of its affiliates. The connections between Cicada3301 and ALPHV suggest that the former may be a rebranded version or closely related to the latter.
Targeting VMware ESXi Systems
Cicada3301 is particularly dangerous because of its focus on VMware ESXi environments. VMware ESXi is widely used in enterprise settings for server virtualization, making it a high-value target for ransomware attacks.
The ransomware includes both Windows and Linux/VMware ESXi encryptors, with the latter being analyzed by Truesec. The ESXi encryptor uses the ChaCha20 cipher to encrypt files and appends a random seven-character extension to filenames, creating ransom notes labeled "RECOVER-[extension]-DATA.txt."
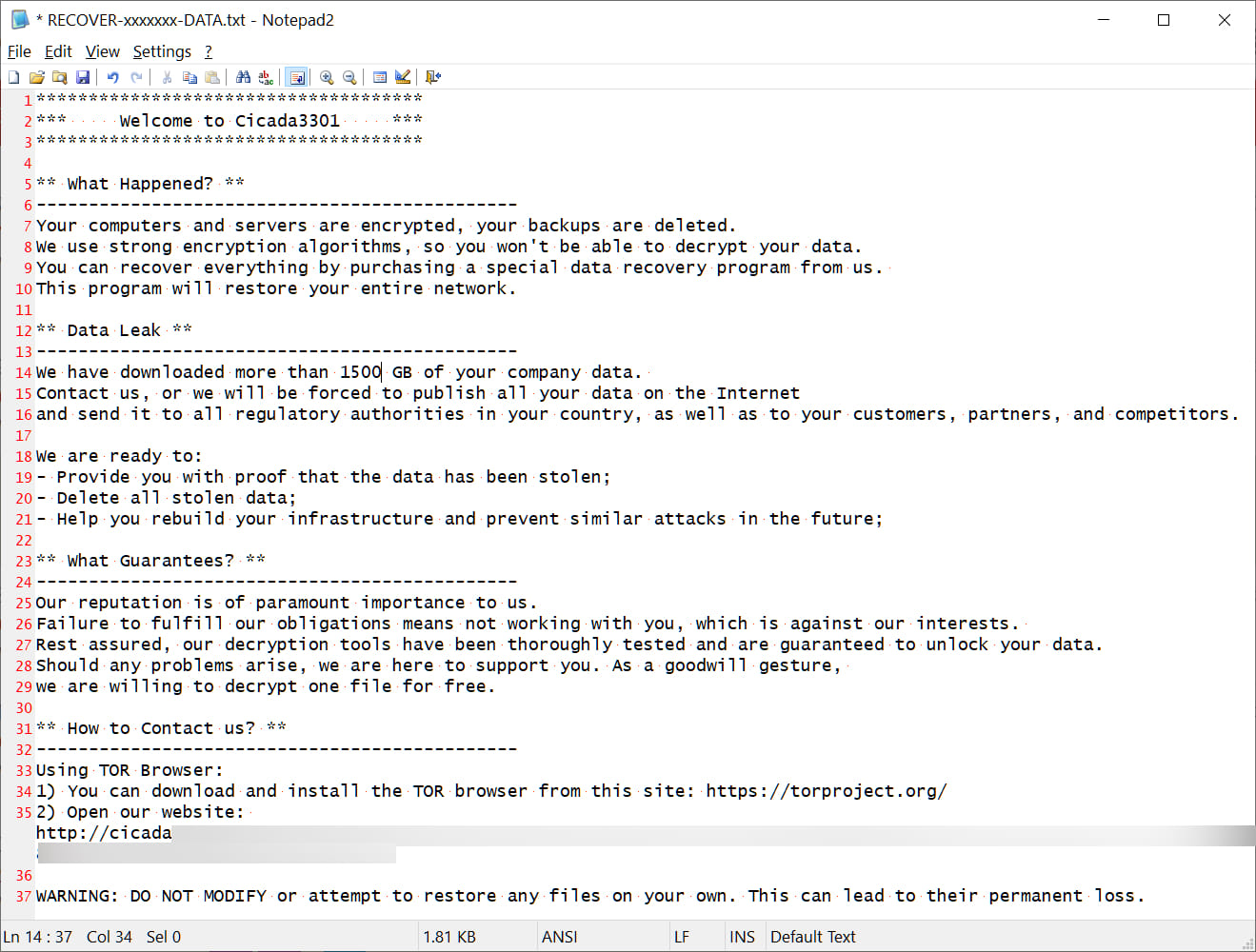
One of the key features of Cicada3301 is its ability to disrupt VM operations. It can shut down virtual machines, delete snapshots, and then encrypt the data, leaving victims with few recovery options. This capability is designed to maximize damage and increase the likelihood that victims will pay the ransom.
Protecting Against Cicada3301 and Similar Ransomware
Given the sophisticated tactics employed by Cicada3301, it is crucial for organizations to take proactive steps to defend against this and similar ransomware threats:
- Regularly Back Up Data: Ensure that backups are stored offline and are not directly accessible from the network. Regularly test the restoration process to verify backup integrity.
- Implement Strong Security Practices: Use multi-factor authentication (MFA), strong password policies, and network segmentation to limit access to critical systems.
- Patch Vulnerabilities: Regularly update and patch software, including VMware ESXi systems, to protect against known vulnerabilities.
- Monitor Network Activity: Deploy advanced monitoring tools to detect unusual activity or potential breaches before they lead to a ransomware attack.
- Educate Employees: Conduct regular cybersecurity training to help employees recognize phishing attempts and other common attack vectors.
Conclusion
The emergence of Cicada3301 underscores the constant evolution of ransomware threats and the need for organizations to stay vigilant. By understanding the tactics used by this group and implementing robust security measures, businesses can reduce the risk of falling victim to this or other ransomware attacks. At Net Protector Cyber Security, we are committed to providing the tools and expertise needed to protect your digital infrastructure from evolving cyber threats.






