Vulnerability in 2 famous WordPress plugins can affect millions of users
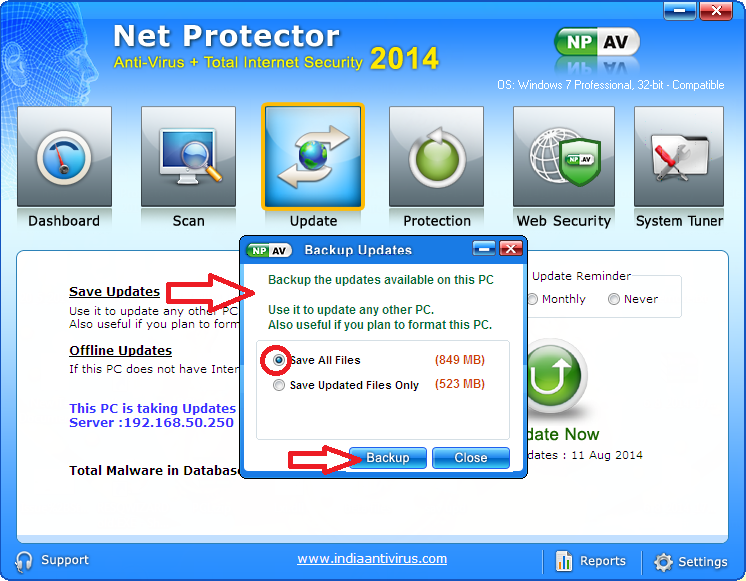
Two of the most famous plugins of WordPress are found to have severe vulnerabilities.
"Elementor Pro" is a site builder that allows users to add modules and customize their site using a drag and drop builder. Recently this plugin was found to allow hackers to install malicious files in the user system. Wordfence has tweeted about the issue being faced:
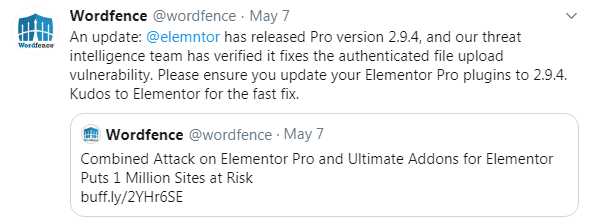
The second plugin found with vulnerabilities is "Ultimate Addons for Elementor". The vulnerability allows the attacker to target the main Elementor Pro without any admin user registration. Wordfence has however released the advisory to update the plugins and have provided with solution in the update.
NPAV recommends users to use proper updated plugins for their site as a trusted provider like WordPress provides the patches through these updates. Use plugins and addons from trusted sources only.
Use NPAV and join us on a mission to secure the cyber world.






