Blogs
-
Read moreCVE-2025-61984 exploits OpenSSH's ProxyCommand by injecting newlines in usernames for RCE, bypassing CVE-2023-51385; targets Bash-like shells in malicious Git submodules during recursive clones. Affects unquoted %r configs (e.g., from Teleport)—upgrade to OpenSSH 10.1, quote '%r', or restrict Git SSH to mitigate.
-
Read moreCISA flags CVE-2021-43226 in Windows CLFS Driver for active exploitation, enabling local attackers to gain SYSTEM privileges via buffer overflows. Impacts Win10/11 & Servers 2016-2022; federal deadline Oct 27—apply updates, monitor Event IDs 4656/4658, and scan for vulnerabilities now.
-
Read moreNew Android RAT on GitHub ("Huckel789/Android-RAT") promises permanent stealth, web-based control from any device, and features like SMS theft, 2FA hijacking, live cams, ransomware—no PC needed. Experts warn of lowered cybercrime barriers; analyze in isolation for defenses.
-
Read moreA hacker alleges stealing Huawei's source code, dev tools, scripts, and manuals in a major breach, offering them on dark web forums—echoing past espionage fears from U.S. warnings, Vodafone backdoors, and NSA hacks. Investigation ongoing amid global security risks.
-
Read moreLayerX uncovers CometJacking, exploiting Perplexity’s AI browser via malicious URLs to steal Gmail/Calendar data—tricks AI into Base64-encoded exfiltration, bypassing safeguards. Urgent call for AI security-by-design amid rising agentic threats.
-
Read moreCVE-2025-43400 enables out-of-bounds writes via malicious fonts, risking app crashes and memory corruption on macOS, iOS, and more—no active exploits yet, but RCE potential. Update to Sequoia 15.7.1 immediately for protection against untrusted files.
-
Read moreTrend Micro uncovers SORVEPOTEL, a worm-like malware exploiting WhatsApp for fast propagation on Windows systems in Brazil—phishing ZIPs lead to account bans and enterprise hits in government, tech sectors. Detect and block early to avoid spam floods.
-
Read moreA breach at Discord's third-party support vendor leaked personal info like names, emails, IP addresses, limited billing details, and scanned photo IDs for some users—no passwords or full cards affected. Discord is investigating and notifying victims; stay alert for phishing.
-
Read moreCVE-2025-56383 exposes Notepad++ v8.8.3 and earlier to DLL hijacking attacks, allowing local code execution via malicious plugins like NppExport.dll. PoC shows persistence risks—update now and monitor for infections until patched.
-
Read moreThe 2026 FIFA World Cup's 48 teams, 104 matches across Canada, Mexico, and USA heighten cyber risks from ransomware and hacktivists, targeting tech-reliant infrastructure. Experts urge collaboration, stable CISA funding, and daily best practices to secure the event.
-
Read moreCheck Point uncovers Iranian-aligned Nimbus Manticore's (UNC1549) spear-phishing campaign hitting defense, telecom, and aviation in Denmark, Sweden, Portugal. Fake job portals deliver MiniJunk backdoor and MiniBrowse stealer via advanced DLL side-loading—boost phishing defenses now.
-
Read moreCybercriminals leverage Dynamic DNS services to evade detection and build persistent command-and-control networks, abusing 70,000+ domains with minimal oversight. APT groups like Fancy Bear and Chinese hackers use obfuscation and rotations—defenders face growing challenges in mitigation.
-
Read moreThe DPDP Act makes employee data protection crucial for India Inc. Learn about compliance, required safeguards (encryption, MFA), and the high cost of data leaks.
-
Posted: September 29, 2025Views: 60Read moreA malicious update to the postmark-mcp server injects a hidden BCC to exfiltrate sensitive emails from thousands of organizations. Koi’s risk engine uncovered the attack, highlighting risks in AI-driven MCP tools. Remove version 1.0.16+ and audit MCP servers now.
-
Read moreMicrosoft uncovers advanced XCSSET variant infecting Xcode projects for macOS devs—adds Firefox data exfiltration, crypto wallet clipboard swaps via AES-encrypted AppleScripts, and LaunchDaemon persistence. Mitigate with updates, Defender for Endpoint, and domain blocks.
-
Read moreMicrosoft exposes AI-driven phishing campaign targeting US organizations: attackers use AI to craft verbose, business-jargon code in SVG attachments disguised as PDFs, hiding credential-stealing payloads behind invisible dashboards and evading antivirus detection.
-
Read moreSolarWinds patches CVE-2025-26399 (CVSS 9.8), a deserialization flaw in Web Help Desk allowing unauthenticated RCE; it's a bypass of CVE-2024-28988. Affects versions up to 12.8.7—upgrade to HF1. Discovered by Trend Micro ZDI; Qualys QID 733223 for detection.
-
Read moreXLab exposes the AISURU botnet, a 300,000-node powerhouse driving 11.5 Tbps DDoS peaks since 2025 via Totolink firmware hacks. Led by Snow, Tom, and Forky, it features ideological Easter eggs; rivals leak evidence amid calls for takedown amid escalating threats.
-
Read moreThreat actors use vulnerable Windows 8.1 WerFaultSecure.exe on patched Windows 11 24H2 to dump unencrypted LSASS memory via PPL bypass, extracting NTLM hashes and passwords for escalation. Zero Salarium details evasion tactics; defenders urged to monitor WER tools and anomalous PPL activity.
-
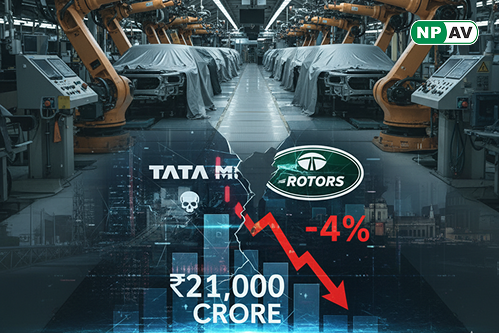
Read moreMajor cyberattack on Jaguar Land Rover (JLR) causes Tata Motors shares to drop 4% to ₹655.30; production paused until Oct 1 with ₹560 crore weekly losses, potential ₹21,000 crore damage—exceeding annual profit. Experts urge cyber insurance and resilient IT amid auto sector digital risks.