Npav Lab
-
Posted: June 13, 2025Views: 51Read moreA 29-year-old man in Mumbai, Tauheed Khan, died by suicide after losing money in an investment fraud and a cyber scam. Discover the tragic details of his story and the ongoing investigation.
-
Read moreAngad Pal Singh, a key suspect in a ₹30 crore export fraud case involving ICICI Bank, has been arrested after 8 years in hiding. Discover the details of the scam and ongoing investigations.
-
Read moreDiscover how the VexTrio scam network exploits WordPress sites to distribute malware and fraudulent schemes. Learn about the tactics used and the impact on global cybersecurity.
-
Posted: June 12, 2025Categories: Bank Phishing, Data Breach, Hacking, Hacker, Banking Trojan, Financial fraud, Fraud ProtectorViews: 76Read moreThe investigation into the ₹11.55 crore cyber fraud at Himachal Pradesh State Cooperative Bank has led to multiple arrests. Learn about the hacking incident, ongoing investigations, and cybersecurity measures.
-
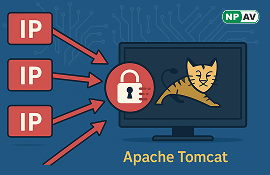
Read moreGreyNoise warns of coordinated brute-force attacks on Apache Tomcat Manager interfaces, involving 295 malicious IPs. Learn about the risks and recommended security measures.
-
Read moreThe Indian government has issued a high-severity alert regarding vulnerabilities in devices using MediaTek processors. Learn about affected devices, security risks, and recommended actions.
-
Read moreA critical vulnerability in Windows Remote Desktop Services (CVE-2025-32710) enables unauthorized remote code execution. Learn about affected systems, security updates, and mitigation strategies.
-
Read moreAdobe has issued a security update addressing 254 vulnerabilities, primarily affecting Adobe Experience Manager. Learn about the critical flaws and how to protect your software.
-
Read moreA new malware campaign disguised as an Instagram growth tool is stealing login credentials. Learn how "imad213" works and how to protect your account.
-
Posted: June 11, 2025Views: 57Read moreFIN6 cybercrime group uses fake resumes hosted on AWS to deliver More_eggs malware via LinkedIn. Learn how they target recruiters and evade detection.