Beware of Microsoft SharePoint Phishing: How to Spot and Stop Attacks on Your Business
.png)
Phishing is a cyber attack that uses fraudulent emails, websites, or messages to trick users into giving away sensitive information such as usernames, passwords, or financial information. One of the most common types of phishing attacks is the use of Microsoft SharePoint. In this blog, we will discuss what phishing using Microsoft SharePoint is, how it works, and how to protect yourself from it.
What is Phishing Using Microsoft SharePoint?
Microsoft SharePoint is a web-based collaboration and document management platform that is widely used in organizations for sharing information and collaborating with team members. Cybercriminals take advantage of the popularity of SharePoint and use it as a tool to trick users into providing sensitive information.
Phishing using Microsoft SharePoint involves creating a fake SharePoint site that mimics the look and feel of a legitimate SharePoint site. The attacker sends a phishing email to the victim, directing them to click on a link that takes them to the fake SharePoint site. The fake site usually contains a login page that prompts the user to enter their username and password. Once the victim enters their login credentials, the attacker can gain access to their account and steal sensitive information. Look at these screenshots

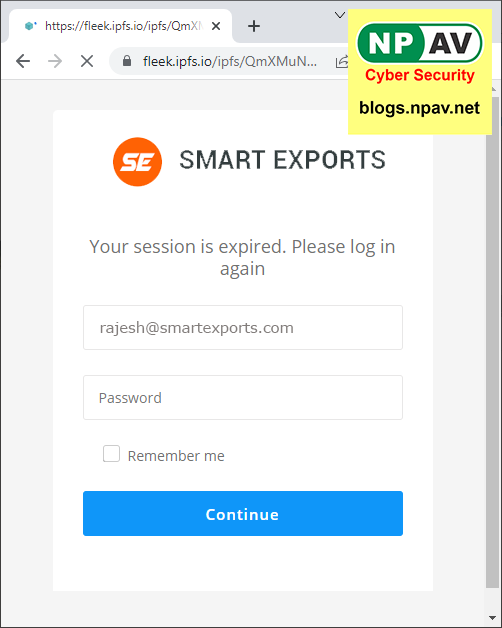
How Does Phishing Using Microsoft SharePoint Work?
- The phishing attack using Microsoft SharePoint follows a few basic steps:
- The attacker creates a fake SharePoint site that looks like a legitimate site.
- The attacker sends a phishing email to the victim, luring them to click on a link that takes them to the fake site.
- The victim clicks on the link and lands on the fake SharePoint site, which contains a login page.
- The victim enters their login credentials on the fake login page, believing it to be a legitimate site.
- The attacker gains access to the victim's account and can steal sensitive information, such as personal or financial data.
How to Protect Yourself from Phishing Using Microsoft SharePoint
Here are some points to protect yourself from phishing attacks using Microsoft SharePoint:
- Be cautious of unexpected or suspicious emails, especially those that ask you to click on a link or provide sensitive information.
- Check the URL carefully before entering any login credentials. Make sure that the URL is legitimate and matches the domain of the organization or service you are trying to access.
- Use multi-factor authentication whenever possible. This will make it more difficult for attackers to gain access to your account even if they do have your login credentials.
- Keep your computer and software up to date with the latest security patches and updates.
- Use a reputable antivirus program and keep it updated.
- Be wary of any requests for personal or financial information, and never provide this information unless you are certain that the request is legitimate.
Phishing using Microsoft SharePoint is a serious threat to online security. Cybercriminals use this tactic to trick users into giving away sensitive information that can be used for fraudulent purposes. By following the tips mentioned above, you can protect yourself from phishing attacks using Microsoft SharePoint or any other type of phishing scam. Always be cautious of unexpected emails, check URLs carefully, and never provide personal information unless you are certain that the request is legitimate. Stay safe online!
- Other (43)
- Ransomware (179)
- Events and News (28)
- Features (45)
- Security (502)
- Tips (83)
- Google (44)
- Achievements (12)
- Products (37)
- Activation (7)
- Dealers (1)
- Bank Phishing (58)
- Malware Alerts (289)
- Cyber Attack (375)
- Data Backup (15)
- Data Breach (219)
- Phishing (188)
- Securty Tips (9)
- Browser Hijack (30)
- Adware (15)
- Email And Password (89)
- Android Security (95)
- Knoweldgebase (37)
- Botnet (20)
- Updates (9)
- Alert (72)
- Hacking (85)
- Social Media (10)
- vulnerability (123)
- Hacker (98)
- Spyware (18)
- Windows (23)
- Microsoft (43)
- Uber (1)
- YouTube (4)
- Trojan (7)
- Website hacks (15)
- Paytm (1)
- Credit card scam (4)
- Telegram (6)
- RAT (12)
- Bug (4)
- Twitter (3)
- Facebook (12)
- Banking Trojan (15)
- Mozilla (2)
- COVID-19 (5)
- Instagram (4)
- NPAV Announcement (17)
- IoT Security (3)
- Deals and Offers (2)
- Cloud Security (12)
- Offers (5)
- Gaming (1)
- FireFox (2)
- LinkedIn (3)
- Amazon (5)
- DMart (1)
- Payment Risk (5)
- Occasion (3)
- firewall (4)
- Cloud malware (3)
- Cloud storage (2)
- Financial fraud (106)
- Impersonation phishing (1)
- DDoS (11)
- Smishing (2)
- Whale (0)
- Whale phishing (4)
- WINRAR (3)
- ZIP (2)
- Fraud Protector (93)
-
Mobile Frauds
(69)
- WhatsApp (19)
- AI (36)






