FedEx Shipment delivery problem – JS malware
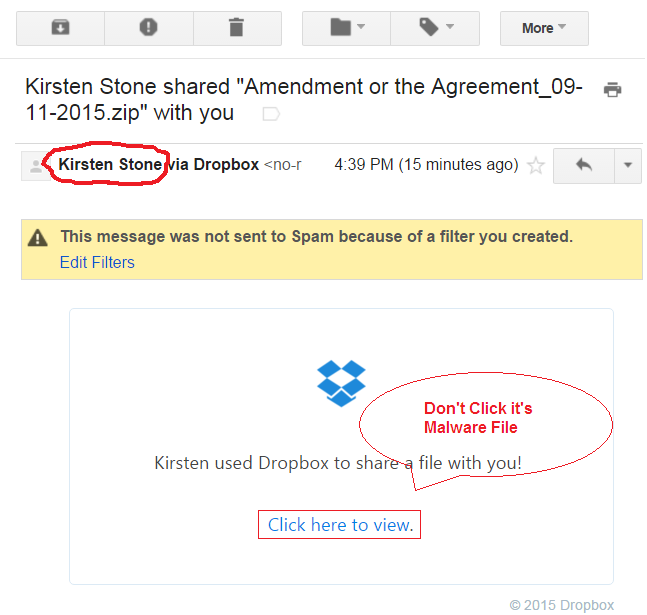
An email with the subject of Shipment delivery problem #0000702101 [ random numbered] pretending to come from FedEx International Next Flight with a zip attachment is another one from the current bot runs which try to download various Trojans and password stealers especially banking credential stealers, which may include cridex, dridex, dyreza and various Zbots, cryptolocker, ransomware and loads of other malware on your computer. They use email addresses and subjects that will entice a user to read the email and open the attachment. Net Protector recommend all the customers, do not click on any malicious attachment please Ignor such a fake emails.
The content of the email says :
Dear Customer,
We could not deliver your parcel. You can review complete details of your order in the find attached.
Regards,
John Cantrell, Sr. Operation Agent.
Dear Customer,
This is to confirm that one or more of your parcels has been shipped. Shipment Label is attached to email.
Regards,
Mitchell Bart, Sr. Station Agent.
Dear Customer,
Courier was unable to deliver the parcel to you. Shipment Label is attached to email.
Thanks and best regards,
Glen Gill, FedEx Station Manager.
Other subjects in this set of malicious malspam include:
Problem with parcel shipping, ID:00000953180
Problems with item delivery, n.0000823595
Unable to deliver your item, #00724372
Other senders pretend to be:
FedEx Standard Overnight
FedEx International MailService
FedEx Ground
FedEx 2Day A.M
These malicious attachments normally have a password stealing component, with the aim of stealing your bank, PayPal or other financial details along with your email or FTP ( web space) log in credentials. Many of them are also designed to specifically steal your Facebook and other social network log in details.
All the alleged senders, companies, names of employees and phone numbers mentioned in the emails are all innocent and are just picked at random. All the shipping, parcel, delivery numbers etc.are random but the number generally matches the attachment number. Some of these companies will exist and some won’t. Don’t try to respond by phone or email.
Attachment consist: Label_00000468516.zip: Extracts to: Label_00000468516.doc.js which download this malicious file 87761567.exe






