GHOSTENGINE: The New Cryptojacking Menace Exploiting Vulnerable Drivers to Evade EDRs

In the ever-evolving landscape of cybersecurity threats, a new cryptojacking campaign dubbed GHOSTENGINE has emerged, showcasing sophisticated tactics to disable endpoint detection and response (EDR) systems and deploy cryptocurrency mining software. This campaign, tracked by Elastic Security Labs as REF4578 and previously known as HIDDEN SHOVEL by Antiy Labs, leverages vulnerable drivers in a method known as Bring Your Own Vulnerable Driver (BYOVD) attack. The primary payload, GHOSTENGINE, represents a significant leap in complexity and stealth for cryptojacking operations.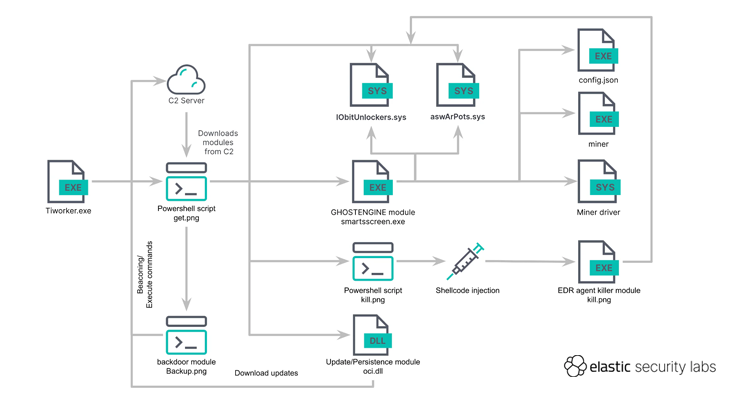
Anatomy of the GHOSTENGINE Attack:
The GHOSTENGINE attack begins with the execution of a file named "Tiworker.exe," which launches a PowerShell script. This script retrieves an obfuscated PowerShell script disguised as a PNG image ("get.png") from a command-and-control (C2) server. The retrieved script then downloads additional payloads, including various executables and system files, from either the C2 server or a backup server via HTTP. The inclusion of an FTP-based fallback mechanism ensures redundancy in payload delivery.
The malicious payloads, such as aswArPot.sys, IObitUnlockers.sys, curl.exe, and others, are executed on the infected system. The malware disables Microsoft Defender Antivirus, clears Windows event logs, and ensures sufficient free space on the C: volume to store downloaded files, which are typically hidden in the C:\Windows\Fonts folder. If necessary, large files are deleted to create space, and alternative volumes are used if the primary one is insufficient.
Ensuring Persistence and Execution
The PowerShell script also establishes three scheduled tasks to maintain persistence:
- Every 20 minutes: Runs a malicious DLL.
- Every hour: Launches the script via a batch file.
- Every 40 minutes: Executes smartsscreen.exe (GHOSTENGINE).
The core of the attack, smartsscreen.exe, uses a vulnerable Avast driver (aswArPot.sys) to deactivate security processes and enable the XMRig miner. Another vulnerable driver from IObit (iobitunlockers.sys) is used to delete security agent binaries, facilitating the execution of the XMRig client downloaded from the C2 server. The PowerShell script "backup.png" functions as a backdoor, allowing remote command execution, while "kill.png" mirrors smartsscreen.exe's capabilities, ensuring redundancy in disabling security agents.
The BYOVD Technique and Broader Implications:
The BYOVD technique, where attackers load a known-vulnerable signed driver to exploit system privileges, is central to the GHOSTENGINE campaign. This method grants attackers high-level access to critical system resources, enabling them to disable security mechanisms effectively. Despite Microsoft's Vulnerable Driver Blocklist in Windows 11 22H2, the list's infrequent updates necessitate manual intervention for optimal protection.
GHOSTENGINE's emergence coincides with another significant discovery: the EDRaser technique, which exploits vulnerabilities in Microsoft Defender (CVE-2023-24860 and CVE-2023-36010) and Kaspersky to manipulate malware detection and deletion processes. Additionally, the HookChain method, which combines IAT hooking, dynamic system service numbers (SSN) resolution, and indirect system calls, further exemplifies the sophisticated tactics cybercriminals employ to evade detection.
The GHOSTENGINE campaign underscores the escalating complexity and ingenuity of modern cyber threats. By exploiting vulnerable drivers and employing sophisticated evasion techniques, attackers can effectively bypass advanced security solutions, highlighting the need for continuous vigilance and adaptive security measures in the cybersecurity landscape. As cryptojacking and other malicious activities become increasingly sophisticated, the importance of robust, updated defenses and proactive threat hunting cannot be overstated.






