GandCrab Ransomware Version 2 !!!!
GandCrab version 2 was released, which contains changes that supposedly make it more secure and allow us to differentiate it from the original version. In this article we will provide a quick overview as to what has changed and how you can identify that you are infected with the GandCrab Ransomware.
What New Changes??
1. In the backend, the biggest change are the hostnames for the ransomware's Command & Control servers.These Command & Control servers need to be accessed before the ransomware will encrypt a computer.
2. Other noticeable changes are the extension used for encrypted files and the ransom note names. With this version of GandCrab, encrypted files will now have the .CRAB extension appended to the file's name.For example, test.jpg will be encrypted and renamed to test.jpg.CRAB.
3. Another change is the ransom note name and it's contents. The new note name is CRAB-Decrypt.txt and now includes instructions on contacting the developers through the TOR instant messaging service.
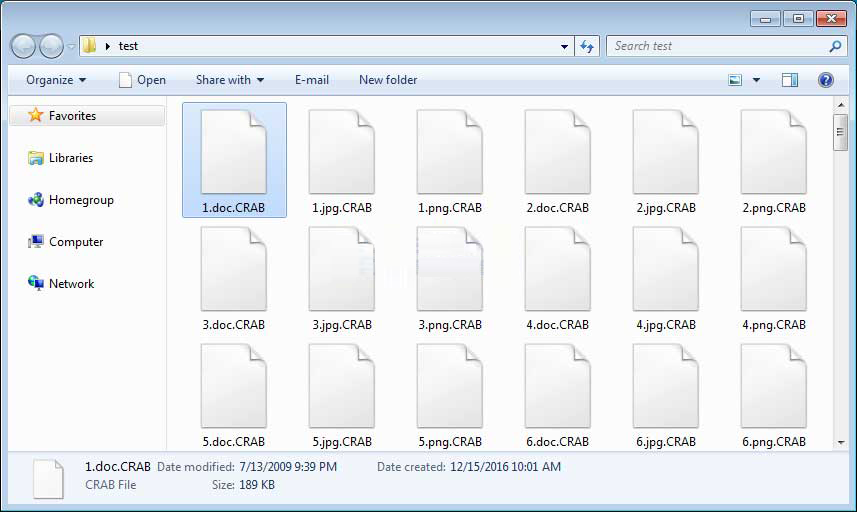
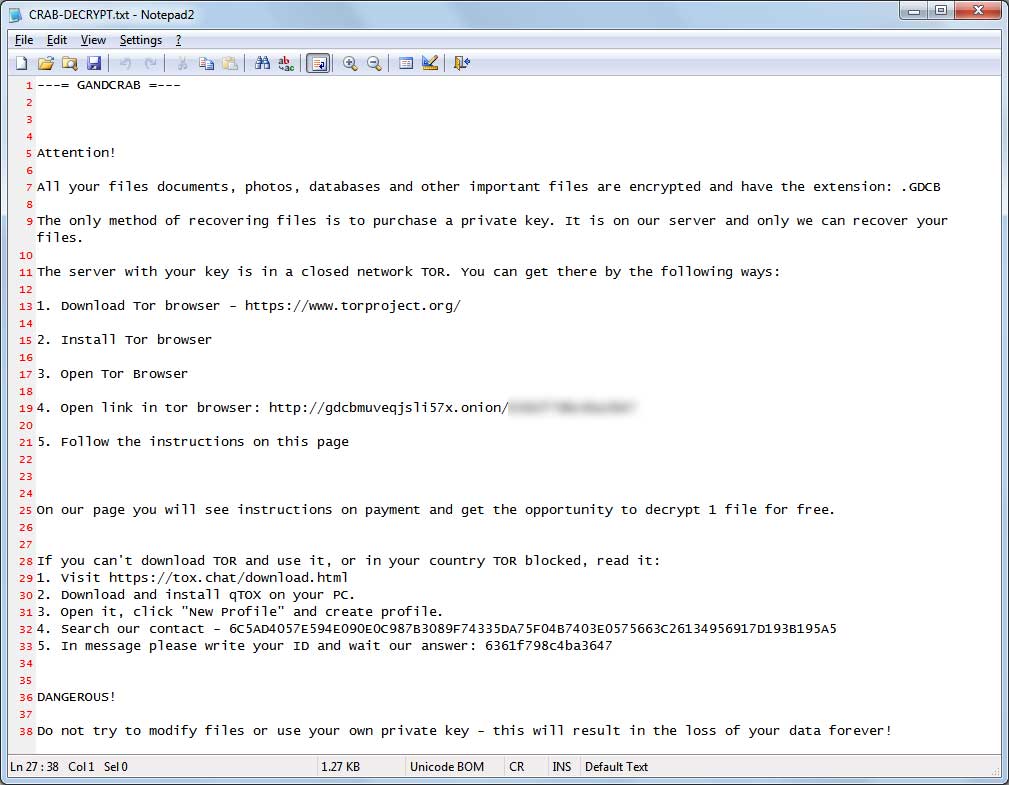
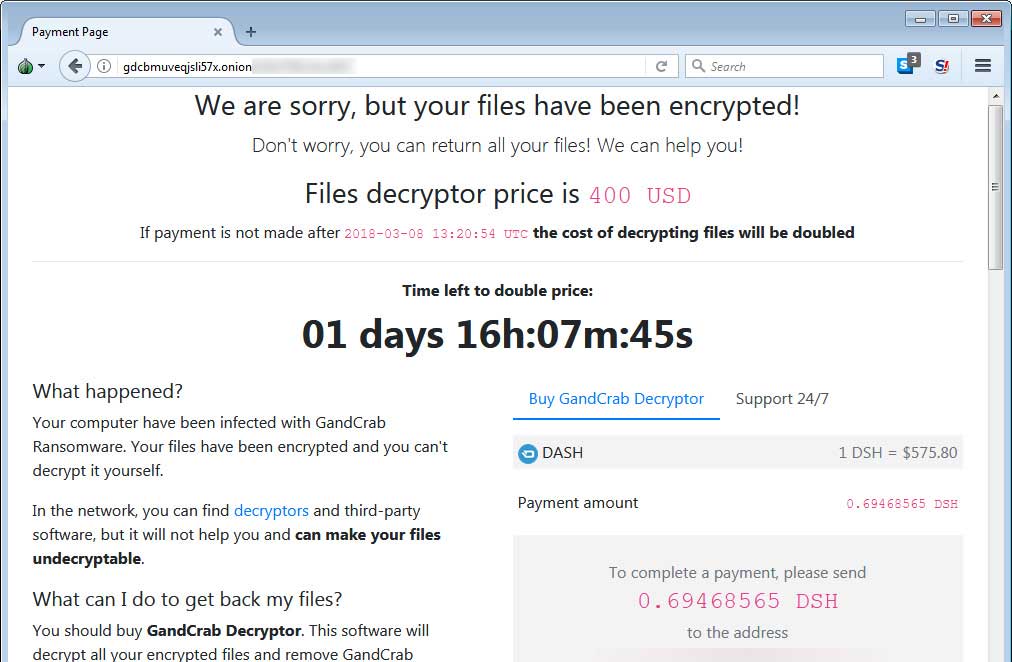
All your files, documents, photos, databases and other important files are encrypted and have the extension:. CRAB
The only way to recover files is to buy a private key. It’s on our server, and only we can recover your files.
All Users are requested to:
- Install and keep NPAV updated up-to-date.
- Make sure NPAV Data Backup is ON.
- Always use trusted and secure sites for downloading setups.






