Indentify Fake Apps in Google Store...
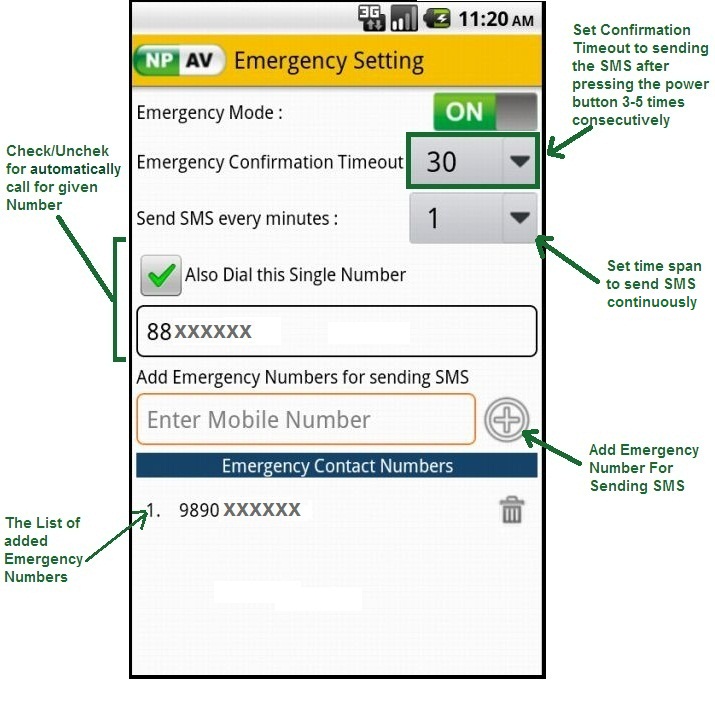
Smart phone users should be very careful while downloading apps from Google store. Because, you can be easily trap by fake and malicious apps. So every user should be very cautious while downloading app from app store. A little awareness about security can save your valuable data from being destructed by viruses and malware attacks.
Here are some tricks which can help you identify fake and malicious app.
- Cross check the developers name on Google. If he is a real developer, he will have some website developments and other valid details.
- Also check developer's profile.
- Always read reviews and rating for that app. This can help you to think on the pros and cons of that app installation.
- You can also ask to Google, whether is it safe to download and install this app or not. Here you can check the quality of that app.
- Do not grant all permissions to app while installing, check first which permissions that app asking for.
For e.g., if a shopping or gaming or wheather app requests access for your SMS, Contacts or emails, do not grant such permissions it can be a malicious app.
1 Comment(s)
Reshma W
Apr 07, 2016 23:21
thx for the information npav team






