New RomCom Variant 'SnipBot' Targets Data Theft Across Multiple Sectors

A dangerous new variant of the RomCom malware, dubbed 'SnipBot', has been spotted in sophisticated data theft attacks. Researchers from Palo Alto Networks' Unit 42 discovered this enhanced version, marking it as RomCom 5.0, and highlighting its ability to steal sensitive data from compromised systems while pivoting on networks to extend the attack.
- Extended Command Set: SnipBot brings 27 new commands that enable precise targeting of file types and directories for data exfiltration. This includes compressing stolen data using 7-Zip and using archive payloads for evasion.
- Advanced Anti-Sandboxing Techniques: SnipBot employs new tricks such as hash checks on executables and checking "RecentDocs" and "Shell Bags" registry keys to evade sandbox detection, further complicating analysis and mitigation.
- Obfuscation via Window Message Control Flow: The malware uses window message-based control flow obfuscation, making it harder to analyze by splitting its code into blocks triggered in sequence.
- Phishing and Fake Download Sites: The attack vectors include phishing emails with links to download files like PDFs, and older vectors involve fake Adobe sites tricking users into downloading malicious files. The attackers use legitimate certificates to evade security warnings when delivering malware from compromised file-sharing platforms.
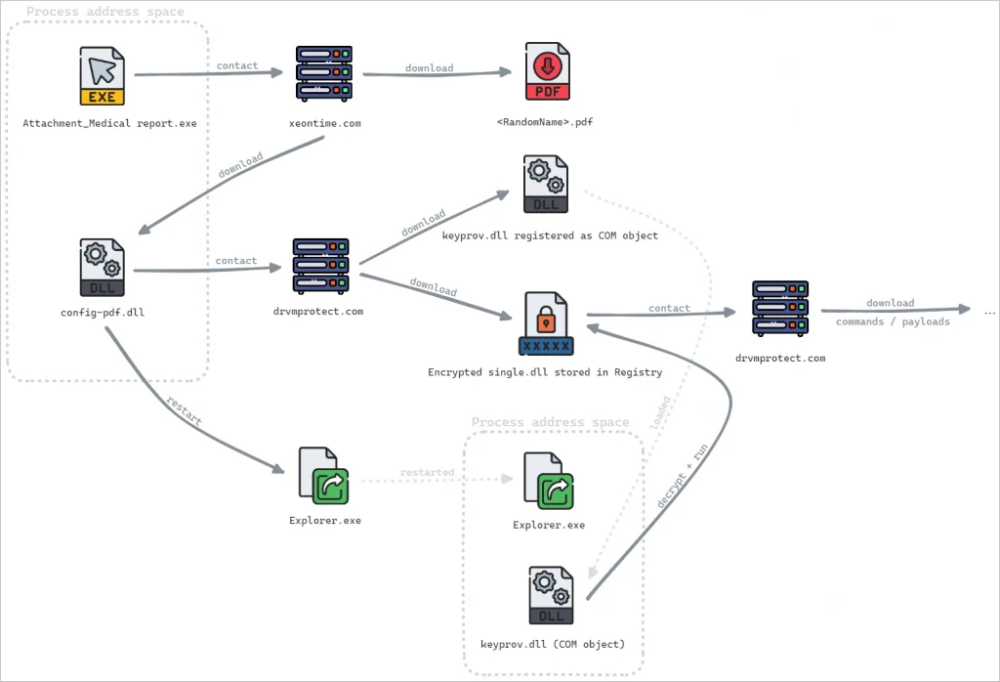
- Stealthy Persistence and Data Theft: Once embedded in a system, the malware uses COM hijacking to inject its payload into "explorer.exe," ensuring persistence across reboots. It then steals files from Documents, Downloads, and OneDrive directories, leveraging tools like AD Explorer to gather network information and PuTTY Secure Copy client for data exfiltration.
The evolution of RomCom into SnipBot reflects the growing sophistication of malware in data theft and espionage campaigns. With new stealth features, network-pivoting capabilities, and targeted sector attacks (including IT, legal, and agriculture), organizations must remain vigilant and strengthen their security protocols to counter this advanced threat.
Comment(s)






