Npav Lab
-
Posted: August 13, 2025Views: 69Read moreA report reveals that Delhi residents have lost INR 1,450 crore to cybercrime over the past decade. Learn about the rising scams and how to protect yourself.
-
Read moreLearn essential tips to secure your smart home IoT devices, routers, and smart speakers. Protect your home from cyber threats and ensure your privacy.
-
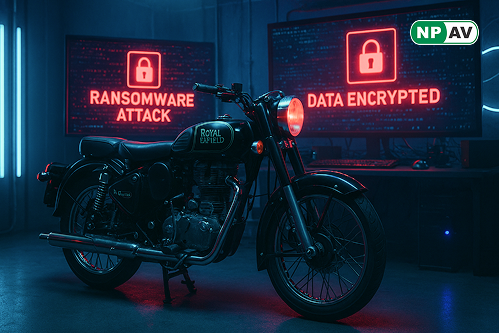
Read moreRoyal Enfield faces a significant ransomware attack, with hackers claiming full system compromise and demanding ransom. Learn about the implications and response.
-
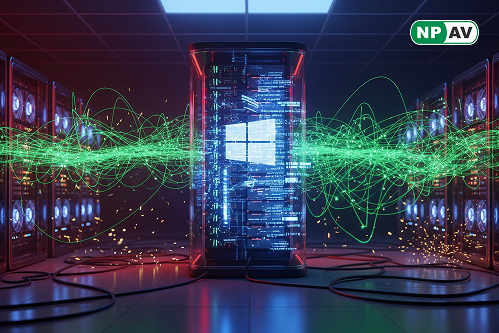
Read moreResearchers unveil the 'Win-DoS Epidemic' at DEF CON 33, revealing new vulnerabilities in Windows that can turn servers and Domain Controllers into DDoS botnets. Learn more about the risks.
-
-
Read moreA serious flaw in a major automaker's dealer portal allows hackers to unlock and start vehicles remotely. Learn about the vulnerability and its implications.
-
Posted: August 11, 2025Views: 105Read moreA DRDO employee in Hyderabad has fallen victim to a fake investment scam on WhatsApp, losing ₹54 lakh. Learn how the scam operated and the warning signs.
-
Read moreGoogle's Salesforce instance was compromised by the ShinyHunters group using voice phishing tactics. Learn about the breach and the exposed records.
-
Read moreHackers exploit a legitimate driver to bypass Microsoft Defender and install Akira ransomware. Learn how this vulnerability works and how to protect your PC.
-
Read moreSocket’s Threat Research Team has uncovered over 60 malicious RubyGems packages that steal social media and marketing credentials. Learn how these infostealer tools operate.