Npav Lab
-
Read moreApple has released critical updates to address CVE-2025-43300, a zero-day vulnerability affecting iOS, iPadOS, and macOS. Learn about the impact, affected devices, and how to stay secure.
-
Read moreFortinet users are being warned of potential cyberattacks targeting their VPN tools. Learn about the latest threats, how to identify them, and steps to take to protect your network.
-
Read moreExplore the resurgence of trojan horses powered by Large Language Models (LLMs). Learn how these threats disguise themselves as legitimate applications, embedding malicious capabilities that challenge traditional defenses.
-
Read moreDiscover PhantomCard, a sophisticated NFC-based Trojan targeting banking customers in Brazil. Learn how this malware exploits NFC relay attacks to steal sensitive card data and facilitate unauthorized transactions.
-
Read moreLearn about the emerging ghost-tapping technique that exploits stolen payment card details linked to Apple Pay and Google Pay. Discover how this method facilitates retail fraud and the impact on users.
-
Read moreDiscover how RingReaper, a sophisticated malware strain, targets Linux environments and evades traditional endpoint detection and response systems using advanced techniques. Learn about its impact on security.
-
Read moreDiscover how the new GodRAT malware, derived from the Gh0st RAT codebase, infiltrates financial institutions using malicious screensaver and program files. Learn about its evolution and impact on security.
-
Read moreA critical vulnerability in Microsoft’s Copilot for M365 has allowed unauthorized access to sensitive files without leaving a trace in audit logs. Learn about the implications for organizations and the lack of transparency from Microsoft.
-
Read moreDiscover how cybercriminals are exploiting brokerage accounts in sophisticated ‘ramp and dump’ schemes using mobile phishing tactics. Learn about the risks and how to protect yourself.
-
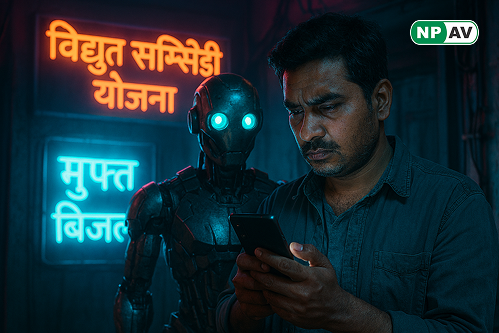
Read moreA new Android phishing campaign is deceiving Indian users by posing as the PM Surya Ghar: Muft Bijli Yojana. Learn how attackers exploit this scheme to install malware and steal sensitive banking information.