Blogs
-
Read moreA series of data breaches linked to the ShinyHunters group has affected major companies like Qantas and LVMH. Learn how voice phishing techniques compromised Salesforce CRM systems and the implications for data security.
-
Read moreAnubis ransomware, first detected in November 2024, targets both Android and Windows platforms, utilizing a ransomware-as-a-service model. Learn about its tactics, high-profile attacks, and how to defend against this emerging threat.
-
Read moreThe maritime industry faces a surge in ransomware attacks from APT groups, with over 100 cyberattacks reported in the past year. Learn about the tactics used by hackers and the implications for global trade.
-
Read moreSonatype reveals a cyber infiltration campaign by the North Korea-backed Lazarus Group, targeting CI/CD pipelines with malicious packages. Learn about the implications for open-source security.
-
Read moreA cybercriminal known as Tsar0Byte claims to have breached Nokia's internal network, stealing sensitive data of over 94,500 employees. Learn about the implications and exposed information.
-
Read moreToxicPanda, a sophisticated Android banking trojan, has infected over 4,500 devices in Europe, targeting banking apps to steal credentials. Learn about its techniques and impact.
-
Read moreA recent cyberattack on a US chemicals company exploited the SAP NetWeaver vulnerability CVE-2025-31324 to deploy Auto-Color malware. Learn about the attack details and key takeaways.
-
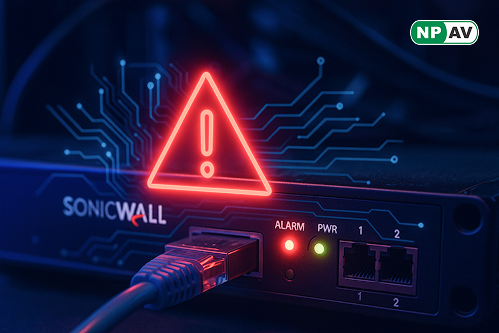
Read moreSonicWall has identified critical vulnerabilities in its SMA 100 series SSL-VPN appliances, allowing remote code execution. Learn about the risks and recommended actions to secure your systems.
-
Read moreA significant data breach at the Tea dating app has compromised the private data of over 11 million female users, including selfies and IDs. Learn more about this serious privacy violation.
-
Read moreDiscover Shuyal, a newly identified stealer malware targeting 19 browsers, including Tor and Brave. Learn how it extracts sensitive data and poses a significant threat to your security.
-
Read moreDiscover the CSRF vulnerability in PaperCut NG/MF that could allow attackers to modify security settings or execute arbitrary code. Learn about recommended actions to mitigate risks.
-
Net Protector Endpoint Security EDR Achieves VB100 Certification for Excellence in Malware Detection
Posted: July 29, 2025Comments: 16Views: 7227Read moreNet Protector Endpoint Security (EDR) by Biz Secure Labs Pvt. Ltd. has earned the prestigious VB100 certification, achieving a 99.08% malware detection rate and a 0.041% false alarm rate. Discover the key highlights of this certification. -
Read moreAeroflot canceled over 40 flights due to a cyberattack claimed by the pro-Ukrainian hacker group Silent Crow. Learn about the impact on operations and the response from Russian authorities.
-
Read moreLearn about the injection vulnerability in Cisco Identity Services Engine (ISE) that could allow remote code execution. Discover recommended actions to mitigate risks and protect your network.
-
Read moreA single compromised password caused the downfall of KNP Logistics, a 158-year-old company, leaving 730 employees jobless. Learn about the Akira ransomware attack and its implications for UK businesses.
-
Read moreA security breach in Amazon's Q Developer Extension for Visual Studio Code affected nearly one million users. Learn how a hacker injected malicious code and what steps Amazon took to resolve the issue.
-
Read moreDiscover the new Gunra ransomware targeting Windows systems, encrypting files, and deleting shadow copies. Learn about its origins, tactics, and how organizations can defend against this emerging threat.
-
Read moreA cyber attack by Pakistani hackers on NIT Jamshedpur's official website displayed anti-India sentiments. Learn about the incident, its implications, and the ongoing investigation into the breach.
-
Read moreA new malware campaign targets gamers by promoting fake indie games through YouTube and Discord, installing credential-stealing malware. Learn how this sophisticated attack operates and the variants involved.
-
Read moreA 43-year-old entrepreneur from Navi Mumbai lost ₹2.29 crore in an online trading scam involving fake financial advisors and a fraudulent trading app. Learn how the scam unfolded and the ongoing investigation.